
Despite the popularity of cryptocurrency, many investors and traders don’t give a second thought to security – Which they pay for dearly. Today we look at the 6 reasons why you need a VPN for cryptocurrency.
Cryptocurrency has been around for over a decade, but it’s fair to say that it only picked up spotlight from the mainstream in 2018, with Bitcoins meteoric rise in the Winter of that year. For the novice investor, this proved to be a costly lesson. Bull runs in any market are destined to end eventually, and cryptocurrency is no different. In January and Februrary 2019, the same bull run became a bear market, and the value of all cryptocurrencies crashes significantly.
This didn’t deter many though, especially those familiar with the ebb and flow of the markets, and those who had believed in the future usability of cryptocurrency.
Those who kept the faith were rewarded, as cryptocurrency saw a massive surge once more during the bulk of the COVID lockdowns. The increasing popularity of NFTs and the Web3 space saw the crypto space gain much-needed use case. No longer a speculative market, cryptocurrency had usage that the average joe on the street could benefit from.
The numbers reflect this. According to statistics website Statistica, the total transaction value in the Digital Payments segment is projected to reach US$8.49tn by the end of 2022. The website also forecast that the total transaction value is expected to show an annual growth rate of 12.31% resulting in a projected total amount of US$15.17tn by 2027.

Despite the massive value cryptocurrency presents, there has been little talk of cybersecurity with regards to cryptocurrency, let alone using a VPN for cryptocurrency.
Anybody who has spent time in the crypto community, especially in the NFT space, knows somebody who has lost out on millions of dollars due to poor security. To this end, we have put together a list of reasons to encourage you to consider a VPN for cryptocurrency transactions, investments, and trading.
VPN FOR CRYPTOCURRENCY – ENCRYPTION
One of the primary uses of a VPN for cryptocurrency is encryption.
Encryption is at the heart of any Virtual Private Network. All VPNs aren’t engineered the same, and depending on the protocols used, a VPN might have different functions, speeds, and vulnerabilities.
The primary role of encryption is make your acitivty inivisble on the net, a huge positive for cryptocurrency. This is done by obsfucating your data – also known as encryption. A VPN with good encryption is one of the strongest digital measures you can take in securing your crypto.
To classify how VPN encryption is used, things like encryption type, protocols, and ciphers used must be considered. These things determine exactly how protection is formed. Each represents a different answer to the cybersecurity question.
There are a lot of moving parts when it comes to this, so we won’t cover them all for the purposes of this article. For ciphers, one of the most powerful choices considering VPN for cryptocurrency is AES-256 (Advanced Encryption Standard). AES is considered the gold standard of encryption ciphers. It is a symmetric block cipher, and is used by the US Government, US Military, and nearly every financial institute in the world. AES is used in software and hardware globally, and is one of the foundational pillars of modern cybersecurity.

It was also taken by the NSA to protect national security systems.
Because of its use by the US government, it became extremeley popular in the private sector, especially as an element of VPN encryption. It is without a doubt the most common choice when looking to setup VPN encryption.
With regards to protocols, using a VPN for Cryptocurrency should be using WireGuard, or the more popular OpenVPN.
OpenVPN is without a doubt the leader when it comes to VPN protocols. It is a protocol but also a software, which uses secure point-to-point and site-to-site connections. Nearly all major VPN providers offer OpenVPN, making it the top dog in the space.
The protocol is responisble for handling client-server communications, and establishes a tunnel between client and software.
OpenVPN handles encryption and authentication, and also uses the OpenSSL extensively. OpenVPN has the option to use either UDP (User Datagram Protocol) or TCP (Transmission Control Protocol) to transmit data.
OpenVPN is best used over UDP, which it will always default to first. It will only attempt TCP if the UDP connection fails.
It uses a custom security protocol that bypass HTTP and NAT.
OpenVPN was the first protocol that championed open-source. Its code isn’t owned by just one entity, and third-parties can always inspect it and continuously improve it. This has lead to some VPN providers building on OpenVPN to build their own custom service, like SaferNet has done.
All in all, OpenVPN is the most popular for a reason. It offers the greatest balance of speed and security, and is truly best-in-class when it comes to using a VPN for cryptocurrency.
VPN FOR CRYPTOCURRENCY – EXTRA PROTECTION FROM HACKERS
To preference this point – The overwhelming majority of VPNs, especially the popular ones, have zero malware protection. This is not always the case, and VPNs like SaferNet do indeed offer comprehensive protection against hackers.
Cybercrime is a huge danger online, more than many internet users know. Cryptocurrency investors and traders are prime targets, given the amount of cash they deal with online.
There are a range of threats online facing cryptocurrency enthuists every second, including:
Ransomware – Ransomware is a virus that encrypts a users device. Following encryption, the user must pay a monetary sum for the return of their device. With regards to using a VPN for Crypto, it is vital that protection is used due to the high amount of ransomware found in the cryptocurrency scene.
Spyware – Spywares main focus is stealing sensitive information from users – Passwords, keys, etc. A VPN for Crypto is invaluable here. Spyware can not only siphon passwords, but also seed phrases which are the final step in accessing an account.
Remote Access Trojans – Remote Access Trojans, or RATs, are very similar to Spyware, however they allow the hacker full control of an infected device. Given their destructive nature, a VPN for crypto is vital in combating RATs.
As stated, the majority of VPNs offer no anti-virus features. This is not the case for SaferNet’s always-on VPN, which was built with twin goals in mind – To offer both the privacy of a VPN and the antivirus capabilities of anti-malware software. While most services require a number of different software solutions to achieve both privacy and security, SaferNet gets it done all-in-one. Given how much cryptocurrency markets and users are targeted, a VPN for cryptocurrency activity is vital.
VPN FOR CRYPTOCURRENCY – PHISHING
Though ordinarily mentioned with malware, the amount of phishing attacks that happen to cryptocurrency investors is so overwhelmingly frequent that it deserves its own entry.
Phishing is perhaps the most well-known attack vector a hacker can utilize. Nearly everyone has seen a phishing attempt at some point in their lives. To put it simply, Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords. Phishing is not necessarily all about grabbing credentials, though. Modern phishing methods often revolve around having the target download a file that is covertly malware or enabling macros on a Word document which in turn deploy a virus. Phishing and the act of social engineering come hand in hand.
Between 2018 and 2019 alone, there was over half a billion dollars stolen in phishing attacks, and to date there has been even more in a series of ledger-based phishing attacks.
While Malware in general can lead to huge losses, its clear that phishing is #1 in cryptocurrency attacks. Everybody can get phished, no matter how savvy they are – When considering a VPN for crytocurrency, phishing protection should be a top concern.
VPN FOR CRYPTOCURRENCY – FIREWALL BYPASS
Firewall bypassing is an issue of contention for many, yet still must be considered when looking at a VPN for cryptocurrency. There are also many technical limitations to be considered. While it is not a use case for the many, it is valid for the few.
Firewalls can be found in schools, universities, and more recently in company offices. They are put in place for security purposes – and rightfully so – but often use elements of control like blocking certain website categories. One of these categories is cryptocurrency, and many organisations with a firewall in place do not allow connected uses to access cryptocurrency websites.
When using a VPN for cryptocurrency, many of these Firewalls can be bypassed, and a user can freely trade and invest while on the network. This of course should be used responisibly, and slacking off on the job or in class to trade crypto using a VPN isn’t advisable!










 2. Next, click on the button that says “Download On The App Store”. or simply go to…
2. Next, click on the button that says “Download On The App Store”. or simply go to…  3. In the Apple App Store, click the “GET” Button and then click “INSTALL”.
3. In the Apple App Store, click the “GET” Button and then click “INSTALL”.
 5. This will install SaferNet to your Android device.
5. This will install SaferNet to your Android device. 7. Enter your SaferNet Username and Password.
7. Enter your SaferNet Username and Password. 8. A Device Setup menu will appear asking you who will be using this device with all available profiles listed.
8. A Device Setup menu will appear asking you who will be using this device with all available profiles listed. 9. Choose the profile that you wish to be loaded onto this device and press “Start Protection.”
9. Choose the profile that you wish to be loaded onto this device and press “Start Protection.” 10. Press “Allow” to add SaferNet VPN Configurations.
10. Press “Allow” to add SaferNet VPN Configurations. 11. You may be required to authenticate your ID to do this.
11. You may be required to authenticate your ID to do this. 12. Success! Congratulations, SaferNet is now monitoring, controlling and protecting your iOS Device!
12. Success! Congratulations, SaferNet is now monitoring, controlling and protecting your iOS Device!
 2. Next, click on the button that says “Get it on Google Play” or simply go to…
2. Next, click on the button that says “Get it on Google Play” or simply go to…  3. In Google play, click the green button that says “INSTALL.” This will install SaferNet to your Android device.
3. In Google play, click the green button that says “INSTALL.” This will install SaferNet to your Android device. 4. Next, open SaferNet on your Android Device.
4. Next, open SaferNet on your Android Device. 5. Enter your SaferNet Username and Password.
5. Enter your SaferNet Username and Password. 6. A Device Setup menu will appear asking you who will be using this device with all available profiles listed.
6. A Device Setup menu will appear asking you who will be using this device with all available profiles listed.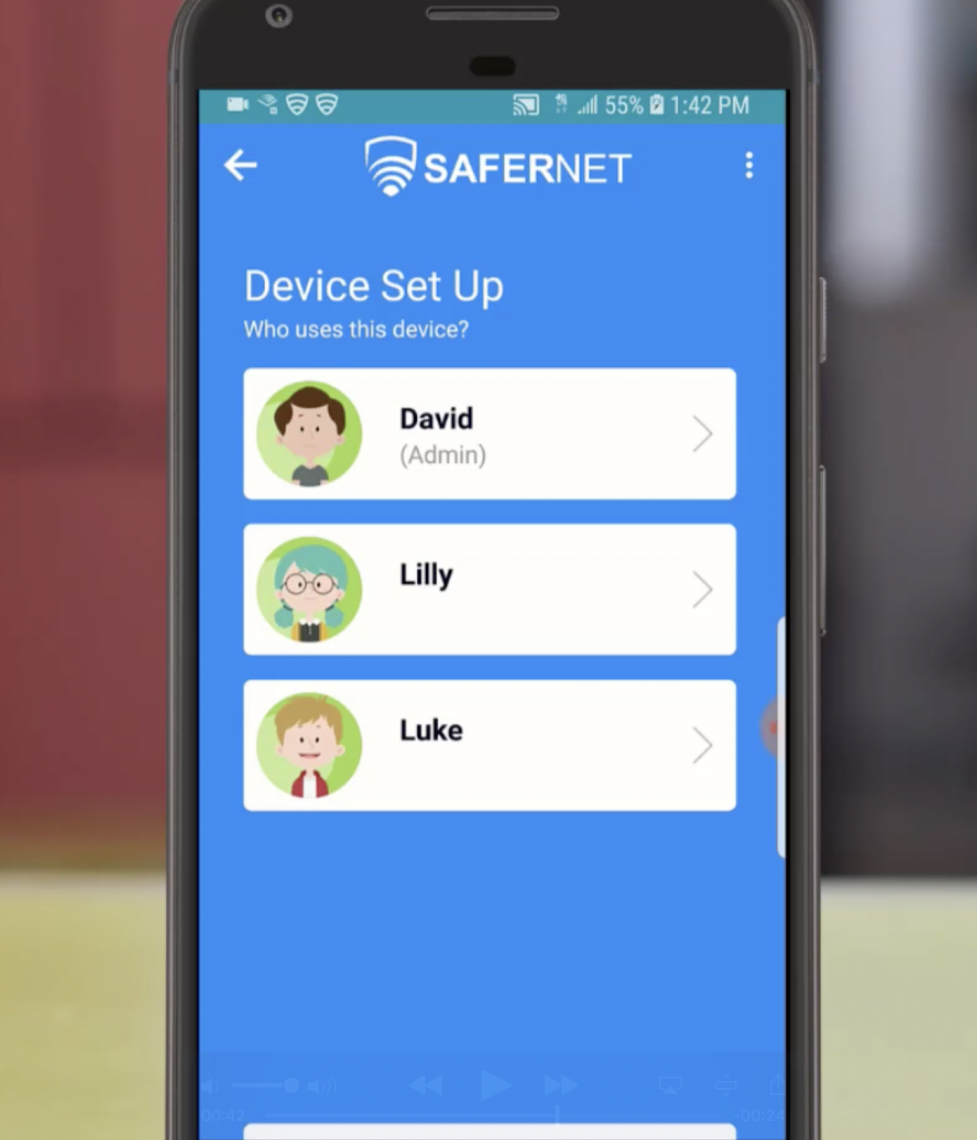 7. Choose the profile that you wish to be loaded onto this device.
7. Choose the profile that you wish to be loaded onto this device. 8. Press OK to the VPN Connection request.
8. Press OK to the VPN Connection request. 9. Success! Congratulations, SaferNet is now monitoring, controlling and protecting your Android Device!
9. Success! Congratulations, SaferNet is now monitoring, controlling and protecting your Android Device!
 2. Next, click on the button that says “Download for Mac” or simply click this link…
2. Next, click on the button that says “Download for Mac” or simply click this link…  3.This will download the SaferNet installation file to your MACOS.
3.This will download the SaferNet installation file to your MACOS. 5. Click on the “SaferNet” icon. A popup dialog box will appear, which states: ““SaferNet” is from an unidentified developer. Are you sure you want to open it?” Click on the “Open” button to proceed
5. Click on the “SaferNet” icon. A popup dialog box will appear, which states: ““SaferNet” is from an unidentified developer. Are you sure you want to open it?” Click on the “Open” button to proceed
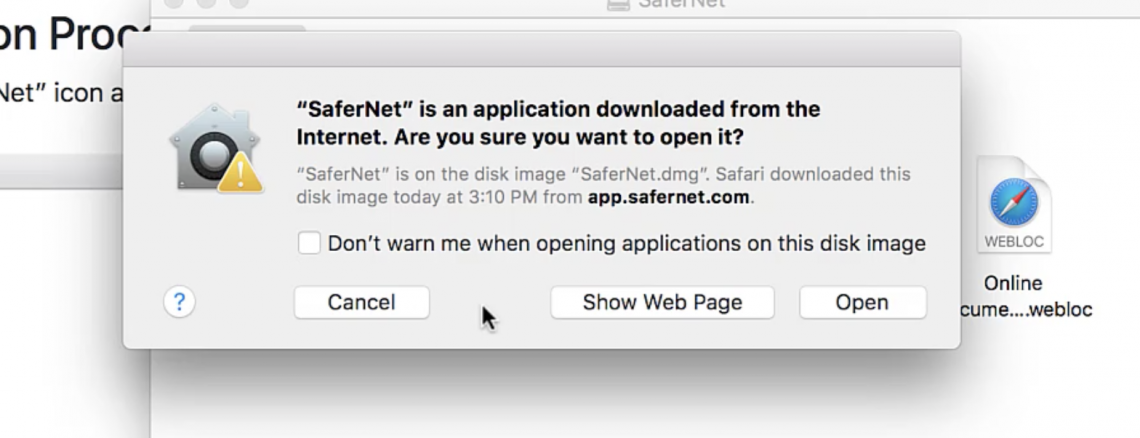 6.Please enter your MacOS credentials, and click OK to start the installation process.
6.Please enter your MacOS credentials, and click OK to start the installation process. 9.A Device Setup menu will appear with all available profiles.
9.A Device Setup menu will appear with all available profiles. 11. Success! Congratulations, SaferNet is now monitoring, controlling and protecting your MAC OS!
11. Success! Congratulations, SaferNet is now monitoring, controlling and protecting your MAC OS!
 4. The windows InstallShield Wizard will execute. Please follow all of the instructions to install SaferNet.
4. The windows InstallShield Wizard will execute. Please follow all of the instructions to install SaferNet. 5. After installation, a SaferNet icon will be placed on your desktop. Double click it to open SaferNet.
5. After installation, a SaferNet icon will be placed on your desktop. Double click it to open SaferNet. 7. A Device Setup menu will appear with all available profiles.
7. A Device Setup menu will appear with all available profiles. 8. Choose the profile that you wish to use on this device.
8. Choose the profile that you wish to use on this device. 9. Success! Congratulations, SaferNet is now monitoring, controlling and protecting your PC!
9. Success! Congratulations, SaferNet is now monitoring, controlling and protecting your PC!