BlackMatter Ransomware has struck Olympus, a leading medical technology company. Olympus announced last week it was investigating a “potential cybersecurity incident” that impacted some of its EMEA (Europe, Middle East, Africa) IT systems last week. The company employs 31,000 individuals worldwide and has been active for over 100 years, making developments in the medical, life sciences, and industrial equipment industries.
“Olympus is currently investigating a potential cybersecurity incident affecting limited areas of its EMEA (Europe, Middle East, Africa) IT systems on September 8, 2021,” the company said in a statement published Saturday, three days after the attack.
“Upon detection of suspicious activity, we immediately mobilized a specialized response team including forensics experts, and we are currently working with the highest priority to resolve this issue. As part of the investigation, we have suspended data transfers in the affected systems and have informed the relevant external partners.”
Olympus also stated that they’re still working to discover the extent of the damage caused by the BlackMatter Ransomware attack.
Though the company themselves have not confirmed BlackMatter Ransomware was the culprit, ransom notes left on impacted systems point to the gang as the perpitrators.
BlackMatter Ransomware was initially considered to be a newcomer on the scene when it appeared in late July 2021, though it is now confirmed that it is simply a rebrand of Darkside Ransomware.
The Darkside operation shut down after the Colonial Pipeline attack earlier this year as the gang were facing pressure from both international law enforcement and the US government.
BlackMatter Ransomware Analysis

This analysis of Darkside was carried out largely by researchers at Cybereason. It was completed before the gang retired. As BlackMatter Ransomware and DarkSide share the same codebase, the analysis is valid.
Like many other ransomware variants, BlackMatter follows the double extortion trend, which means the threat actors not only encrypt the user’s data, but first exfiltrate the data and threaten to make it public if the ransom demand is not paid. This technique effectively renders the strategy of backing up data as a precaution against a ransomware attack moot.
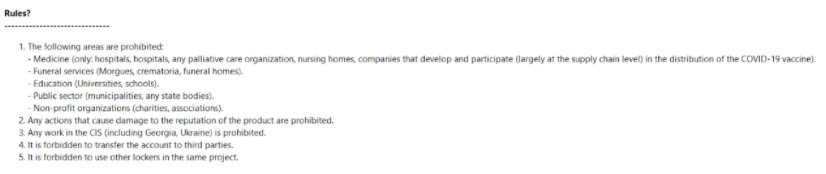
After gaining an initial foothold in the network, the attackers start to collect information about the environment and the company. If it turns out that the potential target is on the attacker’s list of prohibited organizations to attack (ie: hospitals, hospices, schools, universities, non-profit organizations, or government agencies), they don’t move forward with the attack.
If not on the prohibited list, the attackers continue to carry out the operation. The attackers begins to collect files, credentials and other sensitive information, and exfilitrate it. Following this, the attackers use PowerShell to download the BlackMatter Ransomware binary as “update.exe” using the “DownloadFile” command, abusing Certutil.exe and Bitsadmin.exe in the process.
In addition to downloading the BlackMatter Ransomware binary into the C:\Windows and temporary directories, the attacker also creates a shared folder on the infected machine and uses PowerShell to download a copy of the malware there.
After successfully gaining a foothold on one machine in the environment, the attacker begins to move laterally in the environment, with the main goal of conquering the Domain Controller (DC).
Once the attackers make it to the DC, they start to collect other sensitive information and files, including dumping the SAM hive that stores targets’ passwords
In addition to collecting data from the DC, the attackers use PowerShell to download the BlackMatter binary from the shared folder created on the previously infected host.
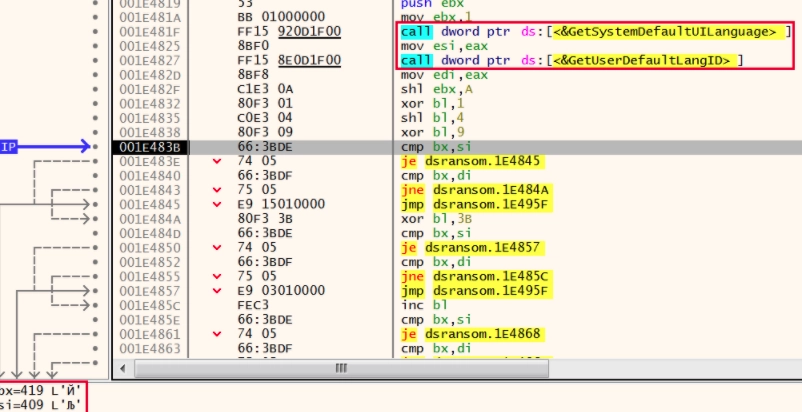
When the BlackMatter ransomware first executes on the infected host, it checks the language on the system, using GetSystemDefaultUILanguage() and GetUserDefaultLangID() functions to avoid systems located in the former Soviet Bloc countries from being encrypted.
After gaining an initial foothold in the network, the attackers start to collect information about the environment and the company. If it turns out that the potential target is on the attacker’s list of prohibited organizations to attack (ie: hospitals, hospices, schools, universities, non-profit organizations, or government agencies), they don’t move forward with the attack.
If not on the prohibited list, the attackers continue to carry out the operation. The attackers begins to collect files, credentials and other sensitive information, and exfilitrate it. Following this, the attackers use PowerShell to download the BlackMatter Ransomware binary as “update.exe” using the “DownloadFile” command, abusing Certutil.exe and Bitsadmin.exe in the process.
In addition to downloading the BlackMatter Ransomware binary into the C:\Windows and temporary directories, the attacker also creates a shared folder on the infected machine and uses PowerShell to download a copy of the malware there.
After successfully gaining a foothold on one machine in the environment, the attacker begins to move laterally in the environment, with the main goal of conquering the Domain Controller (DC).
Once the attackers make it to the DC, they start to collect other sensitive information and files, including dumping the SAM hive that stores targets’ passwords
In addition to collecting data from the DC, the attackers use PowerShell to download the BlackMatter binary from the shared folder created on the previously infected host.
When the BlackMatter ransomware first executes on the infected host, it checks the language on the system, using GetSystemDefaultUILanguage() and GetUserDefaultLangID() functions to avoid systems located in the former Soviet Bloc countries from being encrypted.
Protection
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.