A new Android banking trojan dubbed SOVA (“Owl” in Russian) has emerged and is active development according to researchers at ThreatFabric. Though still in the early stages, SOVA is looking to be extremely sophisticated for Android malware and may pose a serious threat upon release. SOVA seeks to incorporate distributed denial of service (DDoS), man in the middle (MiTM) and ransomware functionality into its arsenal – on top of existing banking overlay, notification manipulation and keylogging services.
Researchers at ThreatFabric note that the hackers ambitions for SOVA are sky-high.
“This malware is still in its infancy [first appearing in August, now only on version 2] and it is undergoing a testing phase…prospecting serious and worrying plans for the near future,” they said in a Friday analysis, noting that the malware’s roadmap is laid out in underground forum posts advertising its availability for testing.
“SOVA is…taking a page out of traditional desktop malware,” they added. “Including DDoS, man in the middle and ransomware to its arsenal could mean incredible damage to end users, in addition to the already very dangerous threat that overlay and keylogging attacks serve.”
Analysis of SOVA showed that the coding and development choices behind the virus are highly sophisticated.
“Regarding the development, SOVA also stands out for being fully developed in Kotlin, a coding language supported by Android and thought by many to be the future of Android development,” according to ThreatFabric. “If the author’s promises on future features are kept, SOVA could potentially be the most complete and advanced Android bot to be fully developed in Kotlin to this day.”
SOVA, like many other malware strains, relies on legitimate software to function. In SOVA’s case, it uses RetroFit for its communication with the command-and-control (C2) server.
“Retrofit is a type-safe REST client for Android, Java and Kotlin developed by Square,” researchers said. “The library provides a powerful framework for authenticating and interacting with APIs and sending network requests with OkHttp.”
SOVA makes use of a banking trojan mainstay – Overlays. However, the malware uses multiple overlays to imitate a number of banking institutes worldwide.
“According to the authors, there are already multiple overlays available for different banking institutions from the U.S. and Spain, but they offer the possibility of creating more in case of necessity from the buyer,” researchers noted. Also, version 2 contains functionality to target users of some Russian banks – drawing ire from other forum users, ThreatFabric reported.
“When it is started for the first time, the malware hides its app icon and abuses the Accessibility Services to obtain all the necessary permissions to operate properly,” researchers explained. Some of those permissions allow it to intercept for SMS messages and notifications for instance, to better hide from the victim – and on the roadmap is also the ability to circumvent two-factor authentication.
One feature that sets SOVA apart from its contemperoarys is its ability to steal session cookies. This allows the virus to piggyback on valid logged-in banking sessions, thus skirting the need to have banking credentials to access victim’s accounts.
Still ahead on the roadmap, SOVA’s authors said that they will soon add “automatic three-stage overlay injections.”
“It is not clear what the three stages imply, but it could mean more advances and realistic process, maybe implying download of additional software to the device,” researchers noted.
ThreatFabric concluded by pointing out that SOVA could become one of the most dangerous threats in the Android ecosystem.
“The second set of features, added in the future developments, are very advanced and would push SOVA into a different realm for Android banking malware,” they said. “If the authors adhere to the roadmap, it will also be able to feature…DDoS capabilities, ransomware and advanced overlay attacks. These features would make SOVA the most feature-rich Android malware on the market and could become the ‘new norm’ for Android banking trojans targeting financial institutions.”
SOVA Analysis
Note: This analysis was carried out by ThreatFabric.
Currently, ThreatFabric identified five samples of SOVA in the wild, with a total of three different malware versions.
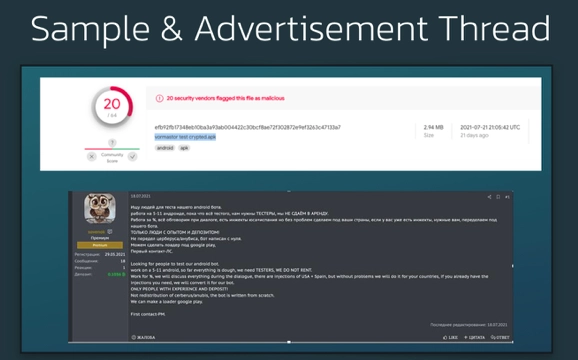
The string highlighted, underneath the file’s hash, is the name the file was uploaded to VirusTotal with. The file name is ‘vormastor test crypted.apk’. As mentioned in the introduction, we conclude that this malware family is still in its testing phase and has been for a few weeks. This is confirmed by a post by the author and seller of SOVA, who was already looking for testers at the end of July.
At the beginning of September, this same user published the first post aimed at selling the bot. In the same thread, the seller is being criticized by other members for having Russian banks within the list of targets. From this thread it also seems that the future versions of this Android malware could switch back to Java, to address some compatibility issues with the obfuscation software they are using.
According to the authors, there are already multiple overlays available for different banking institutions from the USA and Spain, but they offer the possibility of creating more in case of necessity from the buyer.
The main objective of SOVA is to gather the victim’s PII.
SOVA tries its best to remain undetected. To achieve this, SOVA abuses the overlay mechanic to trick victims into revealing their passwords, and other important private information. In an overlay attack, users type their credentials in what they think is a legitimate banking app, effectively giving them to a page controlled by the attacker. SOVA also has the possibility to steal session cookies from the device. This feature is not unheard of but is definitely not common on modern Android Trojans.
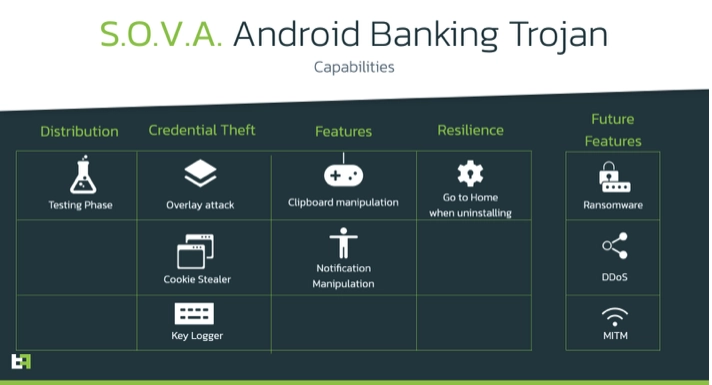
Like most of the banking trojans, SOVA heavily relies on Accessibility Services. When it is started for the first time, the malware hides its app icon and abuses the Accessibility Services to obtain all the necessary permissions to operate properly.
Functionalities of the bot, as advertised by its authors, include:
- Steal Device Data.
- Send SMS.
- Overlay and Cookie injection.
- Overlay and Cookie injection via Push notification.
- USSD execution.
- Credit Card overlays with validity check.
- Hidden interception for SMS.
- Hidden interception for Notifications.
- Keylogger.
- Uninstallation of the app.
- Resilience from uninstallation from victims.
The features that SOVA offers are in line with the standard for Android malware that we are used to see in 2021. However, as previously mentioned, the criminals behind this bot are very proactive and have also released a detailed roadmap of the features to be included in the future releases ofSOVA:
- Automatic 3 stage overlay injections.
- Automatic cookie injections.
- Clipboard manipulation.
- DDoS
- Improved Panel Health.
- Ransomware (with overlay for card number).
- Man in the Middle (MitM).
- Normal Push notifications.
- More overlays.
- VNC.
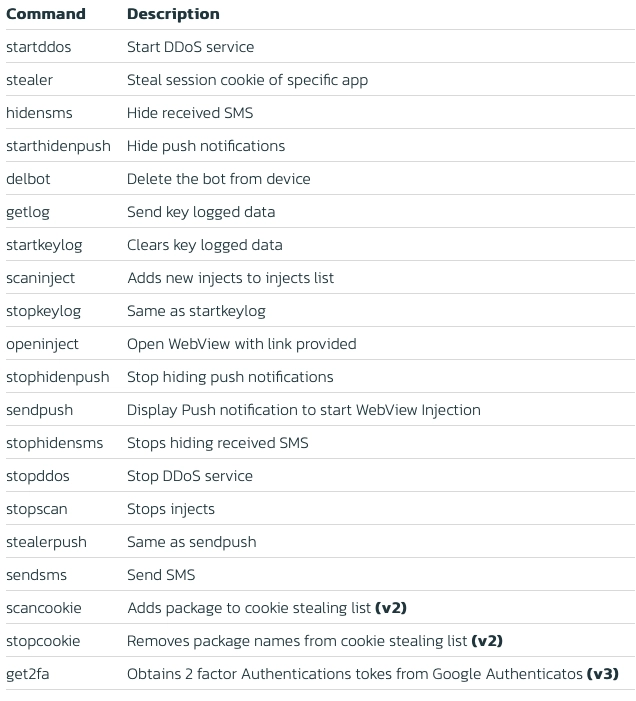
The following list includes all the commands that can be send by the C2 to the bot:
Like the large majority of Android banking trojans, SOVA relies on Overlay attacks to steal PII from its victims. If the user is trying to access a banking application included in SOVAs active target list, the malware will be notified with Accessibility Services, and will display a WebView overlay posing as the intended banking application.
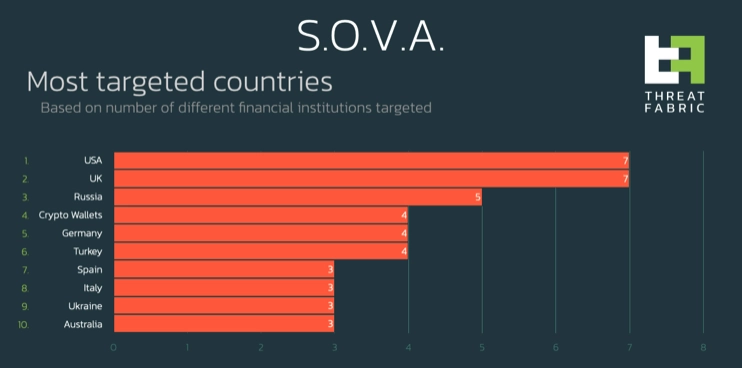
In the following graph you can observe the country distribution of the targets:
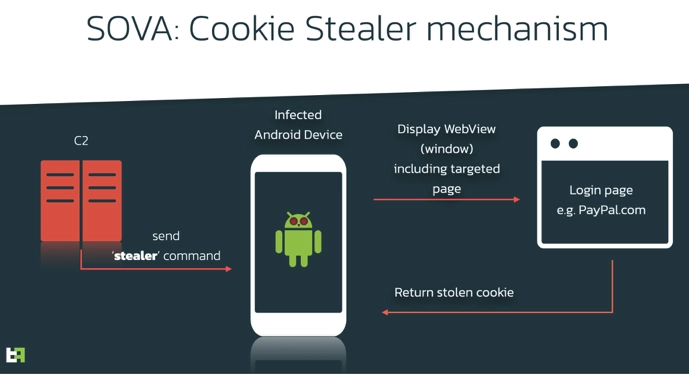
Another interesting feature of SOVA, which is uncommon in Android malware, is the ability to steal cookies. Cookies are a vital part of web functionality, which allow users to maintain open sessions on their browsers without having to re-input their credentials repeatedly. A malicious actor in possession on a valid session cookie has effectively access to the victim’s logged in web session.
Protection
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.