A new multi-OS backdoor malware dubbed SysJoker has been discovered, targeting Windows, Mac, and Linux. Sysjoker has the ability to evade detection in all three environments.
SysJoker was discovered by cybersecurity researchers at Intezer, who first observed its activity in December after investigating an attack on a Linux-based web server.
The researchers have published a detailed report on SysJoker following their investigation.
SysJoker is written in C++, with each variant tailored for its targeted OS. VirusTotal, which uses 57 different antivirus detection engines, wasn’t able to detect any of them.
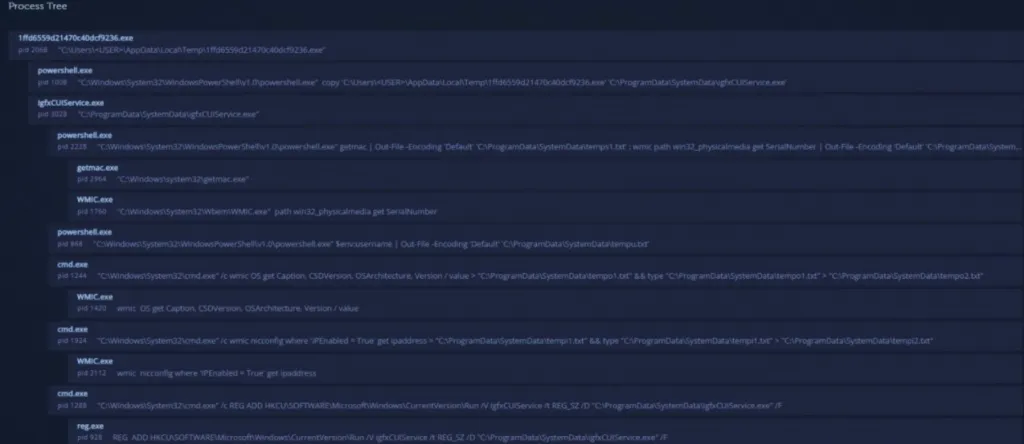
On Windows, SysJoker employs a first-stage dropper in the form of a DLL, which uses PowerShell commands to do the following:
fetch the SysJoker ZIP from a GitHub repository,
unzip it on “C:\ProgramData\RecoverySystem\”,
execute the payload.
The malware then sleeps for up to two minutes before creating a new directory and copies itself as an Intel Graphics Common User Interface Service (“igfxCUIService.exe”).
“Next, SysJoker will gather information about the machine using Living off the Land (LOtL) commands. SysJoker uses different temporary text files to log the results of the commands,” explains Intezer’s report.
“These text files are deleted immediately, stored in a JSON object and then encoded and written to a file named “microsoft_Windows.dll”.”
After gathering system and network data, the malware will create persistence by adding a new registry key (HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run). Random sleep times are interposed between all functions leading to this point.
The next step for the malware is to reach out to the actor-controlled C2 server, and for this, it uses a hardcoded Google Drive link.
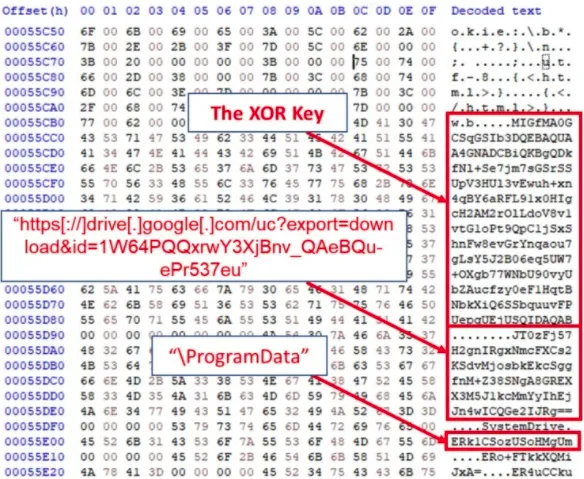
The link hosts a “domain.txt” file that the actors regularly update to provide available servers to live beacons. This list constantly changes to avoid detection and blocking.
The system information collected in the first stages of the infection is sent as the first handshake to the C2. The C2 replies with a unique token that serves as the identifier of the infected endpoint.
From there, the C2 may instruct the backdoor to install additional malware, run commands on the infected device, or command the backdoor to remove itself from the device. Those last two instructions haven’t been implemented yet, though.
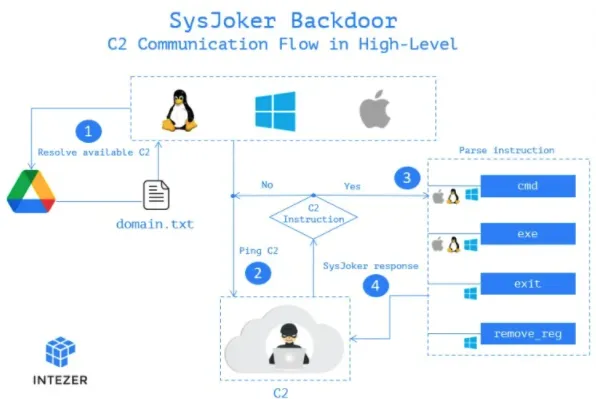
The Linux and Mac variants of SysJoker don’t have the first-stage dropper in DLL form, they do perform the same malicious behaviour.
Intezer has provided full indicators of compromise (IOCs) in their report that admins can use to detect the presence of SysJoker on an infected device.
On Windows, the malware files are located under the “C:\ProgramData\RecoverySystem” folder, at C:\ProgramData\SystemData\igfxCUIService.exe, and C:\ProgramData\SystemData\microsoft_Windows.dll. For persistence, the malware creates an Autorun “Run” value of “igfxCUIService” that launches the igfxCUIService.exe malware executable.
On Linux, the files and directories are created under “/.Library/” while persistence is established by creating the following cron job: @reboot (/.Library/SystemServices/updateSystem).
On macOS, the files are created on “/Library/” and persistence is achieved via LaunchAgent under the path: /Library/LaunchAgents/com.apple.update.plist.
The C2 domains shared in the Intezer report are the following:
- https[://]bookitlab[.]tech
- https[://]winaudio-tools[.]com
- https[://]graphic-updater[.]com
- https[://]github[.]url-mini[.]com
- https[://]office360-update[.]com
- https[://]drive[.]google[.]com/uc?export=download&id=1-NVty4YX0dPHdxkgMrbdCldQCpCaE-Hn
- https[://]drive[.]google[.]com/uc?export=download&id=1W64PQQxrwY3XjBnv_QaeBQu-ePr537eu
If you found that you have been compromised by SysJoker, follow these three steps:
- Kill all processes related to the malware and manually delete the files and the relevant persistence mechanism.
- Run a memory scanner to ensure that all malicious files have been uprooted from the infected system.
- Investigate the potential entry points, check firewall configurations, and update all software tools to the latest available version.
Protection Against Threats Like SysJoker
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.