Phishing attacks have long been the bane of consumer households, and in recent years have switched their target to Small and Medium Businesses (SMB). The number of Phishing attacks rose notably at the start of the pandemic when many workers began working-from-home. That increase has been somehow overshadowed by recent developments, as a new report by GreatHorn reveals Phishing attacks are up nearly 6000% since October. The increase is believed to be tied to a variation in attack vector for hackers carrying out phishing; Malformed URLs.
Many SMBs train their employees to look out for phishing practices in suspect emails. One of the most obvious practices is Typosquatting. This is a ubiquitous attack vector used by cybercriminals, where a misspelling will appear on a brand name website in the hopes the victim will fall for it. One example may be having “facebaok.com” instead of “facebook.com.”
Usually, a hacker will ‘sit’ on a domain like this, hoping someone will accidentally access the site. More common, however, is using it within a phishing email. People don’t always closely scrutinize the URL of a received email and often fall for the trick. As mentioned, this practice is reasonably well-known and not as successful as it once was.
The natural evolution of this and the vector that has caused such a staggering increase in phishing attacks is Malformed URLs.
Usually, on a website that has security certification, you will see “https://”, and if the certification is not in place “http://” appears. For a Malformed URL, the prefix will look something like “http:/\”, using a forward-slash followed by a back-flash, instead of two back-flashes.
While it may seem obvious written in this format, there are a couple of reasons why it’s so successful.
How Malformed URL Phishing Emails Trick Victims
With any form of attack via email, the first and arguably largest obstacle the hacker has to circumvent is the email server itself. Many reputable email providers such as Outlook have security features built-in to ensure their users either don’t receive a malicious email or that the emails are placed in spam or junk.
These security features will scan the incoming URL for suspicious elements, and either reject the email entirely or mark it as spam.
Malformed URLs entirely bypass these scans. Email security is only in place to examine the body of the domain rather than the hypertext protocol preceding it. This security follows a list of guidelines called “Known Bad” which checks a series of conditions on an email before deciding how to handle it, and HTTP-checking is omitted.
The second hurdle a hacker must pass is one less-easily defined and much less tangible, and that is the suspicion of the victim and how well they can eye-ball URLs. The human brain is a complex machine, and amongst many of its odd features is the ability to detect things through eyesight that aren’t there or are inaccurate. Our periphery vision can quite easily match to form the same pattern as what’s in our direct line of sight.
This can be seen most clearly in Uniformity Illusions. This concept applies to reading, and in this case reading data, namely a URL. If we quickly parse a URL with our eyes looking for Typospotting, our periphery will rarely spot “http:/\” unless we intentionally look for it.
What The Attacks Look Like
Greathorns’ report states that across the board, SMBs running Microsoft Office 365 were more likely to witness these attacks at a much higher rate than those running other email services.
While many competitors are catching up, Office 365 remains the dominant email provider for SMBs, and so these attacks are widespread.
Greathorn provided an example of one such attack. The URL used was “http:/\brent.johnson.australiasnationalskincheckday.org.au//exr/[email protected]”. This specific phishing attempt impersonates a voicemail service, informing the recipient that they have a voice message. It emulates the appearance and behavior of many email platforms that use cloud-based voicemail services.
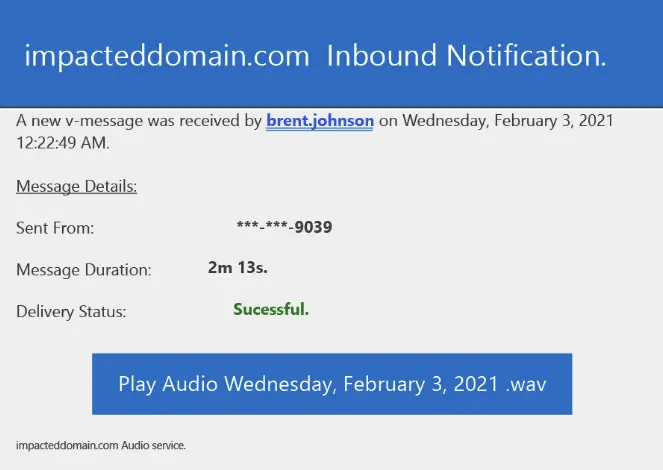
Part of the phishing email, with the button linking to the malformed URL which many users would not pick up on
Following the link brings a user to a ‘Office 365’ page, which first contains a reCAPTCHA, a common security feature of legitimate websites, showing the sophistication and subtlety of the attempted attack.
Following this, the user is presented with a high-fidelity replication of an Office-365 login. Their email address will already appear, and they are prompted for a password. Entering the password here will provide hackers with complete login credentials. At this point, the hacker has a free pass; they gain access to the recipient’s email contact lists and other sensitive data, including cloud storage.
The Challenge of Phishing Attacks for SMBs
Phishing as an attack is relative simple to carry out for a cybercriminal. Set up the page, create the email, and start sending it out enmasse to emails. This ease has made phishing become the go-to attack method for targetting SMBs.
At the end of last year, Proofpoint published a report on the state of phishing attacks against SMBs in 2020. The results were troubling, finding that 75% of SMBs faced phishing attacks through the year, and 57% of these attacks were successful.
Many of these were spear phishing and whaling attacks – Specified attacks against managers and C-level executives at a business.
Phishing is without a doubt one of the great threats any SMB must deal with in the world of cybersecurity. Beyond educating employees and performing regular internal security audits, employers should equip themselves with the right tools to combat phishing.
SaferNet is one of these tools, which we engineered with attacks like Phishing in mind.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.