Purple Fox Malware is making the rounds by using a malicious Telegram For Desktop installer, which is further used to install additional malware payloads on infected devices.
The malicious installer is compiled in a script named “Telegram Desktop.exe” that drops two files – the malicious downloader and an actual Telegram installer.
The legitimate installer is not executed, and instead, a downloader is run (TextInputh.exe).
When TextInputh.exe is executed, it will create a new folder (“1640618495”) under “C:\Users\Public\Videos\” and connect to the C2 to download a 7z utility and a RAR archive (1.rar).
The files contain the Purple Fox Malware payload, as well as configuration files. It also unpacks everything into the ProgramData folder.
As detailed in an analysis by Minerva Labs, TextInputh.exe performs the following actions onto the compromised machine:
- Copies 360.tct with “360.dll” name, rundll3222.exe, and svchost.txt to the ProgramData folder
- Executes ojbk.exe with the “ojbk.exe -a” command line
- Deletes 1.rar and 7zz.exe and exits the process
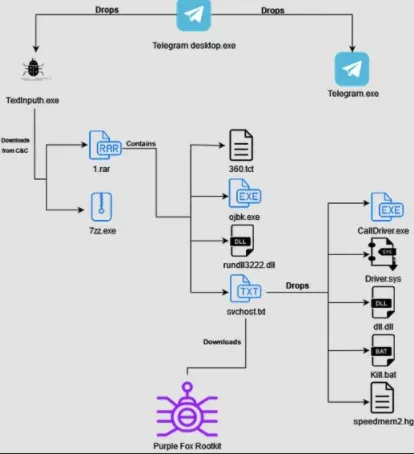
Next, a registry key is created for persistence, a DLL (rundll3222.dll) disables UAC, the payload (scvhost.txt) is executed, and the following five additional files are dropped onto the infected system:
- Calldriver.exe
- Driver.sys
- dll.dll
- kill.bat
- speedmem2.hg
The purpose of these extra files is to collectively block the initiation of 360 AV processes and prevent the detection of Purple Fox Malware on the compromised machine.
The next step for the malware is to gather basic system information, check if any security tools are running on it, and finally send all that to a hardcoded C2 address.
Once this reconnaissance process is completed, Purple Fox Malware is downloaded from the C2 in the form of an .msi file that contains encrypted shellcode for both 32 and 64-bit systems.
Upon execution of Purple Fox Malware, the infected machine will be restarted for the new registry settings to take effect, most importantly, the disabled User Account Control (UAC).
To achieve this, the dll.dll file sets the following three registry keys to 0:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
ConsentPromptBehaviorAdmin
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\EnableLUA
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\PromptOnSecureDesktop
Disabling bypassing UAC is vital because it gives any program that runs on the infected system, including viruses and malware, administrator privileges.
In general, UAC prevents the unauthorized installation of apps or the changing of system settings, so it should stay active on Windows at all times.
Disabling it permits Purple Fox Malware to perform malicious functions such as file search and exfiltration, process killing, deletion of data, downloading and running code, and even worming to other Windows systems.
At this time, it is unknown how Purple Fox Malware is being distributed but similar malware campaigns impersonating legitimate software were distributed via YouTube videos, forum spam, and shady software sites.
Protection Against Purple Fox Malware
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.