Flagpro Malware is being used against Japanese companies by cyber-espionage hacker group BlackTech. BlackTech uses Flagpro Malware in the initial stage of an attack to conduct network reconnaissance. Using Flagpro Malware in this way, BlackTech aim to evaluate the target’s environment and download additional malware to the network.
The attack vector starts with a phishing email written specifically for the target organization, pretending to be from a trustworthy source.
The email carries a password-protected ZIP or RAR attachment that contains a Microsoft Excel file (.XLSM) laced with a malicious macro. Running this code creates an executable in the startup directory, the Flagpro Malware.
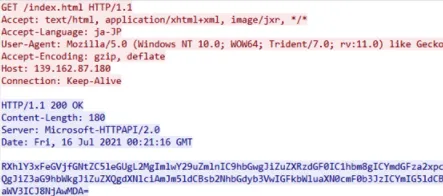
On its first execution, Flagpro Malware connects to the C2 server via HTTP and sends system ID details obtained by running hardcoded OS commands.
In response, the C2 can send back additional commands or a second-stage payload that Flagpro can execute.
The communication between the two is encoded with Base64, and there’s also a configurable time delay between connections to avoid creating a pattern of identifiable operations.
According to a report by NTT Security, Flagpro Malware has been deployed against Japanese firms for more than a year, since at least October 2020. The most recent sample the researchers could retrieve is from July 2021.
The targeted entities are from various sectors, including defense technologies, media, and communications.
NTT researchers noticed a new version of Flagpro Malware, which can automatically close dialogs relevant to establishing external connections that could reveal its presence to the victim.
“In the implementation of Flagpro v1.0, if a dialog titled “Windows セキュリティ” is displayed when Flagpro accesses to an external site, Flagpro automatically clicks OK button to close the dialog,” explains the NTT Security report.
“This handling also works when the dialog is written in Chinese or English. It indicates the targets are in Japan, Taiwan, and English-speaking countries.”
BlackTech were first spotted in 2017, and are believed to be State-Sponsored Hackers operating from China.
Its typical targets are in Taiwan, although it occasionally attacked companies in Japan and Hong Kong to steal technology.
In February 2021, a Unit 42 report connected BlackTech to WaterBear; another cyber-espionage group believed to be backed by the Chinese government.
As an APT, BlackTech possesses the knowledge and sophistication to adjust its tools to new reports like this one, so Flagpro Malware will likely now be modified for stealthier deployment.
As the NTT report concludes: “Recently, they (BlackTech) have started using other new malware called “SelfMake Loader” and “Spider RAT”. It means that they are actively developing new malware.”
Protection Against Flagpro Malware
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.