VPN’s, or virtual private networks, have nearly become a household term in recent times. Once being used almost exclusively by businesses, VPNs found favor with journalists and freelancers who needed anonymity for one reason or another, and eventually became popular in countries where Internet censorship and restrictions began to take place. Fast forward to the 2010s, VPNs evolved and gave themselves purpose to appeal to nearly every type of Internet user; be they ordinary people looking to stream on geo-locked services, individuals with privacy concerns, or small businesses trying to set up a cybersecurity solution with minimum overhead. Today, escaping the VPN is nearly impossible – YouTubers, Podcast Hosts, and even TV talk-show hosts are all endorsing various VPN companies. It’s easy to view VPN’s are an add-on for security, but in actuality they’ve become a necessity; the bare minimum of cybersecurity is no longer sufficient to remain secure in an increasingly connected society.
At a purely basic level, a VPN is used to encrypt your data and add a layer of privacy to protect your identity. Often, VPN’s are described as a ‘tunnel’ that your connection enters and accesses the web through. Usually when you connect to the internet, you do so via your internet service provider (ISP) and your connection is unprotected. In this state, the data you send to the internet is visible to anyone. This includes the the IP address of your device, your location, device information, and often times passwords and other private credentials. This is where the vulnerability lies; the most obvious man in the middle who wants to intercept your data here are hackers, but in the modern age you also have to deal with governments, advertisers, and even your own ISP. This is where a VPN comes in.
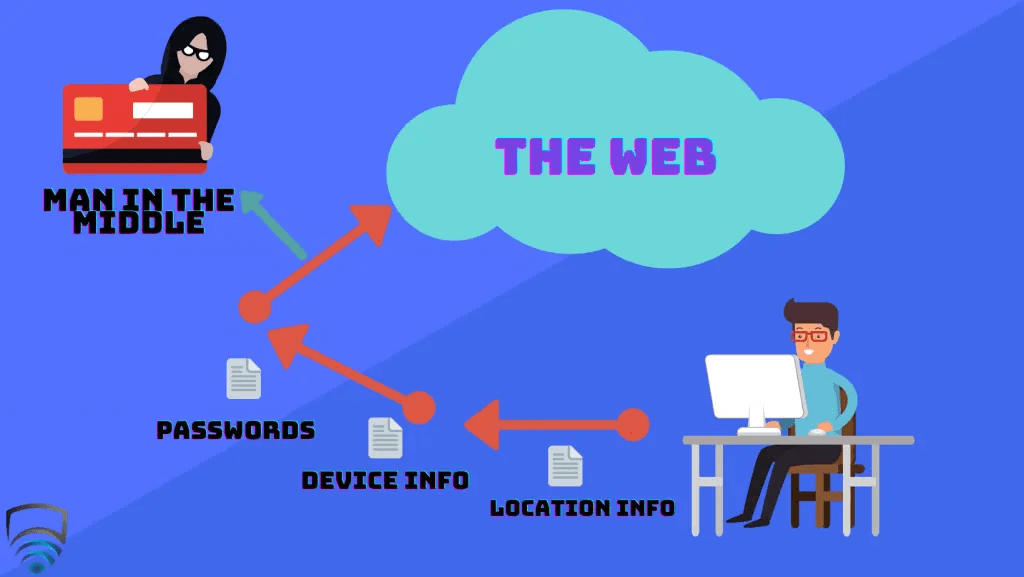
With an active VPN, the data no longer directly goes from your device and to the Internet. Instead, the data first goes through the VPN’s server, and then to the Internet. The connection between your device and the Internet is now in this ‘tunnel’ we mentioned earlier. The key here is that if an entity in the middle does try intercept your data, all they will see is encrypted traffic – Obfuscated information that makes little sense to the viewer, and in the majority of cases, cannot be deciphered. Any party that requests your data would instead be lead the VPN server, and your footprint remains anonymous. Many VPN companies opt to host their servers in a wide variety of locations and this is probably what VPN’s are most known for to everyday people – Location spoofing. Very simply, when you access a VPN server in a different location such as another country, when the VPN server directs your data to the Internet is appears as if you are active from that new location. This has a range of benefits, mostly commonly to view geo-locked streaming services, or booking hotels and flights who’s price vary depending on the buyers location.
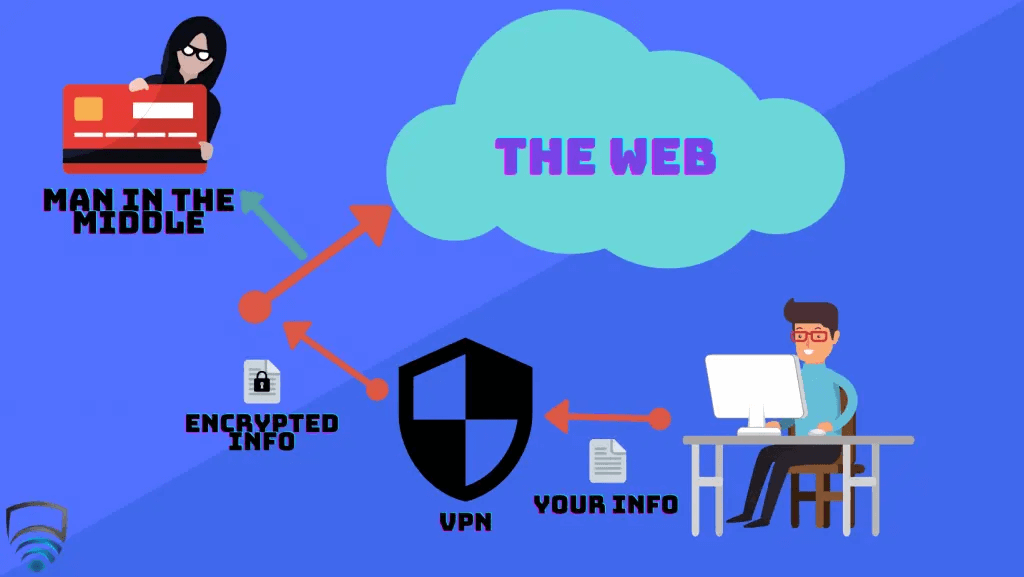
In non-technical terms, Encryption Protocols and Ciphers are what define the strength, complexity, and resilience of the ‘tunnel’ that protects your data when using a VPN. This is where some VPN companies differ; Though there are certainly industry-standards for both Protocols and Ciphers, different companies may choose different options for a variety of reasons. OpenVPN is a standard Protocol used by most VPN providers, which itself makes use of TLS and SSL Protocols. IKEv2/IPsec also provides comprehensive VPN coverage and is engineered for clients that swap connections often, which makes it ideal for mobile devices. L2TP/IPsec, a proprietary Microsoft Protocol, has it’s uses especially for legacy devices, but can easily be blocked by system administrators and has generally slow performance. SSTP, another Microsoft Protocol, offers the advantages of OpenVPN but is mostly only available on Windows devices. SSTP also suffers from being closed-source, which makes it difficult to scrutinize by researchers. The decision for what Cipher to take is much easier – Advanced Encryption Standard (AES) is the industry standard across the board, offering both AES-128 and AES-256; the latter being more favorable. ‘256’ refers to it’s key-length, and brute forcing through this would take billions of years to run through each possible combination. Overall, the average end user shouldn’t be overly concerned with what types of Protocol and Cipher are being used – Any of the above mentioned will trump an unprotected connection at any time.

As VPN’s evolve into a more consumer friendly product, they have become a key weapon in any cybersecurity toolkit. Ten years ago VPN’s were marketed to the public with primarily location spoofing in mind, but VPN’s offer much more now, including malicious website blocking via DNS filtering, as well as parental controls. Businesses have made use of modern VPN’s not just for their inherit cybersecurity, but for their network monitoring capabilities to keep an eye on employees. The same is said for families running parental controls, where parents can now have a view into what their children are viewing online. Cybersecurity is an ever-changing industry, and there are alternatives to VPN’s rising and falling frequently – What’s clear is that given their low-cost, easy setup, and pure accessibility, VPN’s have their role in our online society, and are here to stay.