In January, it came to light that state sponsored hackers attacked US-Based cybersecurity researchers. As of February 1st, Google researchers believe the attack is still on-going; a part of a larger campaign by the government of North Korea that has been happening for many months.
The attack was carried out via social engineering, followed by an attempt to install malware on the target’s machine, which would act as a backdoor. With this backdoor in place, the culprits would be able to gather intel on the researchers work; possibly around vulnerability the research community as a whole were working on.
Attack Methodology
Twitter Account belonging to one of the attacks
In order to gain trust within the research community, the hackers created Twitter accounts – These were linked to their own “research” blogs. From these accounts they would share what you’d expect from a researcher – tweets on their own research including videos, retweets from other researchers, and links to their own blogs and others.
These actions helped build credibility and a sense of legitimacy in their Twitter accounts.
As their blogs increased in popularity, they often has guest bloggers – Legitimate individuals from within the research community. This, again, helped the hackers credibility.
Once they had established themselves on Twitter, the next phase began. The hackers started to reach out to researchers on Twitter via private message.
The state sponsored hackers proposed to the target that they should collaborate on research together. Once the target seemed interested, the conversation would then continue via Telegram.
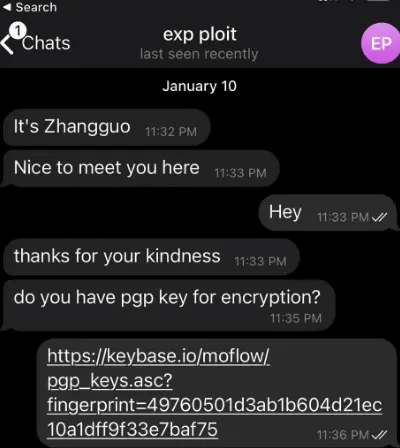
Conversation on Telegram between one of the hackers and researcher Richard Johnson
The collaboration was around vulnerability research, and the hacker would provide the target with a Visual Studio Project. Within the Project was the exploit source code, and a DLL. Upon installation, the DLL would immediately begin to communicate with domains controlled by the hackers. Together, these would provide a backdoor into the researchers machine.
It is currently unknown how many targets the attacks were successful on. One such target, cybersecurity researcher Richard Johnson, had run the Project on a Virtual Machine (VM), and was unscathed.
Additional Attack Vectors
Since details of the initial attacks became public, Google’s Threat Analysis Group (TAG) have identified a separate attack vector linked with the same state sponsored hackers.
The blogs created by the hackers were shared on numerous socials – Reddit, LinkedIn, Discord, and the aforementioned Twitter.
Specifically, one blog titled ‘DOS2RCE: A New Technique to Exploit V8 NULL Pointer Dereference Bug’ was shared from October 14th 2020 onward. It was discovered by Microsoft that the simple act of clicking the link to this blog would deploy malware to the victims browser. The malware would reach back to the hackers controlled domains and execute malicious javascript. It is thought that the attack was successful on a up-to-date versions of Chrome, leading Google to remark that it took advantage of a zero-day vulnerability.
Identity of the state sponsored hackers

It is suspected the attackers behind these events are a part of ZINC, which works under Lazarus Group. Lazarus Group first came into the public spotlight when they carried out Operation Troy, which ran between 2009 and 2012.
Operation Troy was a series of distributed denial-of-service (DDos) attacks targeting government establishments in Seoul, South Korea.
Lazarus Group made the news again, identifying themselves as ‘Guardians of Peace’, in November 2014 for carrying out the Sony Pictures hack. During the attack, confidential data of many Sony Pictures employees were released, and initially circulated on Reddit. This attack is notable in the history of Lazarus Group; it was carried out in a sophisticated and complex manner, showing the group were now developing their skills rapidly.
Lazarus Group have also been responsible for a number of digital bank-heists; and the amount seized is believed to be at least $97 million.
The WannaCry ransomware attack of 2017, which saw a number of healthcare systems including the NHS in the UK brought to a halt, is believed but not confirmed to have been carried out by Lazarus Group.
As of today, Lazarus Group are involved in a number of additional attacks, notable the late-2020 pharmaceutical company attacks. By using spear-phishing methods, members of Lazarus Group acted as health officials and reached out to a number of pharmaceutical companies. Once trust was gained, Lazarus Group sent a number of malicious links to the companies. It is unconfirmed what the goal of the attack was, but it is suspected that they were looking to sell data for profit, extort the companies and their employees, and give foreign entities access to proprietary COVID-19 Research.
State sponsored hackers in the past
State sponsored hackers have been one of the largest forces behind cyberattacks for decades. Other notable state sponsored hackers include Bureau 121, Cozy Bear, The Shadow Brokers, Iranian Cyber Army, Red Apollo, and Equation Group – to name a few.
While state sponsored hackers have been known to the authorities and others in the industry for many years, they became a headline when The Shadow Brokers stole a number of tools from the National Security Agency in 2016. Many of the tools have since been sold to other groups, and now form a cornerstone of many attacks we hear of today.
A notable attack carried out by state sponsored hackers carried out recently was the Solar Winds attack. The attack had been on-going for many months before detection, with many outlets naming it as the ‘Deadliest cyberattack in US History’ due to its scale.
Looking Forward
Attacks carried out by state sponsored hackers often leave long-lasting ripples, and this one by Lazarus Group is no exception. The sense of distrust in the cybersecurity research community has began to grow, though an attack like this can eventually bring a community closer together. In terms of silver-linings, best security practices have been brought to the front such as running Projects and other files within a VM.
Both Google & Microsoft are continuing their research into this incident, as are the cybersecurity researchers on Twitter – the good ones. How far this has reached remains yet to be seen.