Hackers are leveraging controls from the popular messaging app Telegram to make use of a Remote-Access-Trojan (RAT). Dubbed ToxicEye RAT, it can give a hacker access to control a victim’s device via a Telegram bot even if the app is not installed on the victim’s devices. ToxicEye can take over file systems, load other malware such as ransomware, and steal data from the device, according to a new report by Check Point. Researchers have tracked more than 130 attacks in the last 90 days that used ToxicEye RAT. Hackers use the messaging service to communicate with their own server and return data to it.
Telegram, the cloud-based IM platform has enjoyed a surge in popularity this year because of controversial changes to its rival, WhatsApp’s privacy settings. Telegram was the most downloaded app worldwide for January 2021 with more than 63 million installs and has surpassed 500 million monthly active users. This popularity also extends to the cyber-criminal community. Malware authors are increasingly using Telegram as a ready-made command and control (C&C) system for their malicious products because it offers several advantages compared to conventional web-based malware administration.
“We believe attackers are leveraging the fact that Telegram is used and allowed in almost all organizations, utilizing this system to perform cyber attacks, which can bypass security restrictions,” researchers said.
According to researchers, there are a couple of reasons why Telegram is being used for malware like ToxicEye RAT:
- Telegram is a legitimate, easy-to-use and stable service that isn’t blocked by enterprise anti-virus engines, nor by network management tools
- Attackers can remain anonymous as the registration process requires only a mobile number
- The unique communications features of Telegram mean attackers can easily exfiltrate data from victims’ PCs, or transfer new malicious files to infected machines
- Telegram also enables attackers to use their mobile devices to access infected computers from almost any location globally.
The first use of Telegram as an attack vector was by the Masad info-stealer in 2017. The criminals behind Masad realized that using a popular IM service as an integral part of their attacks gave them a number of operational benefits. Since Masad became available on hacking forums, dozens of new types of malware that use Telegram for C&C and exploit Telegram’s features for malicious activity, have been found as ‘off-the-shelf’ weapons in hacking tool repositories in GitHub.
ToxicEye RAT Infection Chain and Functionality

The analysis of the infection chain and functionality was carried out by Check Point.
In the first steps of ToxicEye RAT, the hacker will create a Telegram account and a Telegram ‘bot’. A Telegram bot account is a special remote account with which users can interact by Telegram chat or by adding them to Telegram groups, or by sending requests directly from the input field by typing the bot’s Telegram username and a query.
The bot is embedded into the ToxicEye RAT configuration file and compiled into an executable file. Any victim infected with this malicious payload can be attacked via the Telegram bot, which connects the user’s device back to the attacker’s C&C via Telegram.
In addition, ToxicEye RAT can be downloaded and run by opening a malicious document seen in the phishing emails called solution.doc and by pressing on “enable content.”
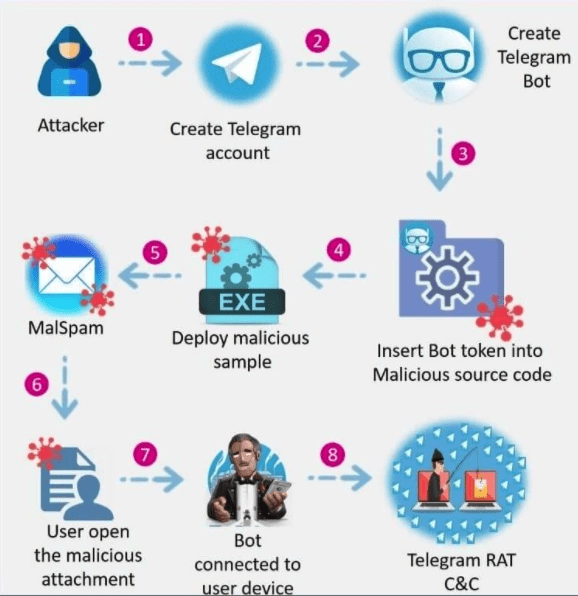
ToxicEye RAT Infection Chain
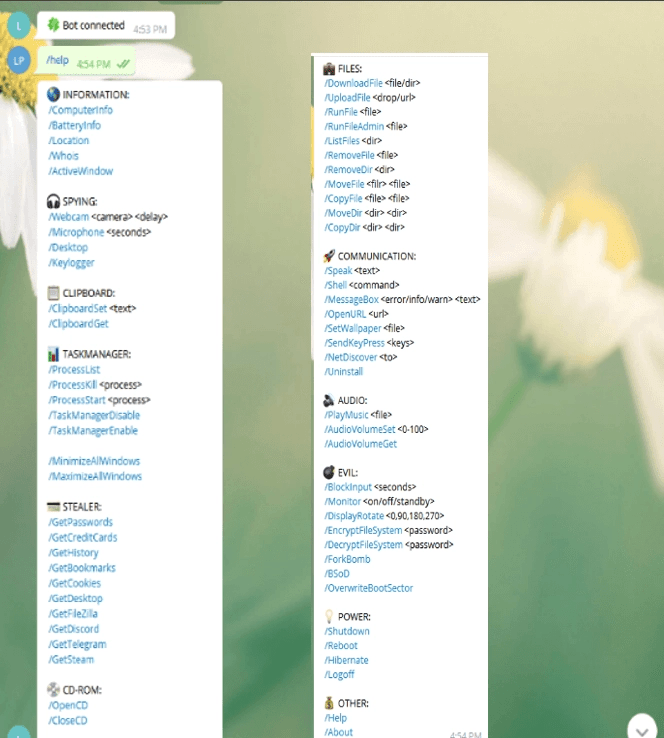
RATs created using Telegram have many shared modules. However, some of the more dangerous like ToxicEye RAT have several key capabilities that distinguish them from the rest:
- Data stealing features – the RAT can locate and steal passwords, computer information, browser history and cookies.
- File system control – Deleting and transferring files, or killing PC processes and taking over the PC’s task manager.
- I/O hijacking – the RAT can deploy a keylogger, or record audio and video of the victim’s surroundings via the PC’s microphone and camera, or hijack the contents of the clipboard.
- Ransomware features – the ability to encrypt and decrypt victim’s files.
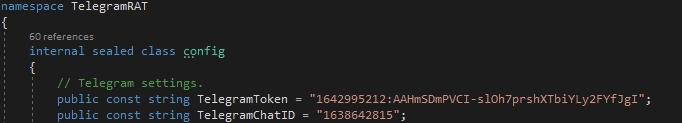
A functionality snippet example from chosen Telegram Rat project
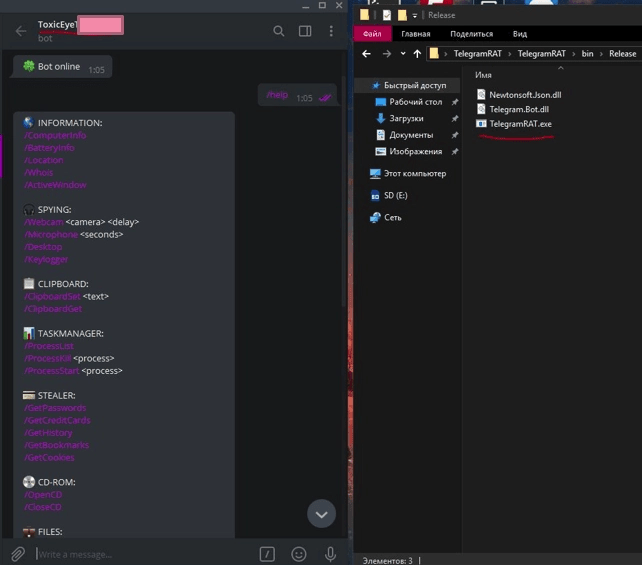
Given that Telegram can be used to distribute malicious files or as a C&C channel for remotely controlled malware, researchers expect that ToxicEye RAT will be one of many.
Protection & Mitigation
There are several steps for protection and mitigation if you feel you may be infected with ToxicEye RAT:
- Search for a file called C:\Users\ToxicEye\rat.exe – if this file exists on your PC, you have been infected and must immediately contact your helpdesk and erase this file from your system.
- Monitor the traffic generated from PCs in your organization to a Telegram C&C – if such traffic is detected, and Telegram is not installed as an enterprise solution, this is a possible indicator of compromise
- Beware of attachments containing usernames – malicious emails often use your username in their subject line or in the file name of the attachment on it. These indicate suspicious emails: delete such emails, and never open the attachment nor reply to the sender.
- Undisclosed or unlisted recipient(s) – if the email recipient(s) has no names, or the names are unlisted or undisclosed – this is a good indication this email is malicious and / or a phishing email.
- Always note the language in the email – Social engineering techniques are designed to take advantage of human nature. This includes the fact that people are more likely to make mistakes when they’re in a hurry and are inclined to follow the orders of people in positions of authority. Phishing attacks commonly use these techniques to convince their targets to ignore their potential suspicions about an email and click on a link or open an attachment.
- Deploy an automated anti-phishing solution – Minimizing the risk of phishing attacks to the organization requires tools that can spot decoy emails containing attacks like ToxicEye RAT better than the human eye. One of these tools is SaferNet.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.