Hackers have breached popular code analysis platform Codecov, modifying the Bash Uploader script and exposing sensitive information in customers’ continuous integration (CI) environment. The attack went unnoticed for some time; Codecov noticed the breach in April, yet the modifications were made in early January. Codecov provides tools that help developers measure how much of the source code executes during testing, a process known as code coverage, which indicates the potential for undetected bugs being present in the code. It has a customer base of more than 29,000 enterprises, including Alibaba, Amazon, Atlassian, Washington Post, GoDaddy, Royal Bank of Canada, and Procter & Gamble.
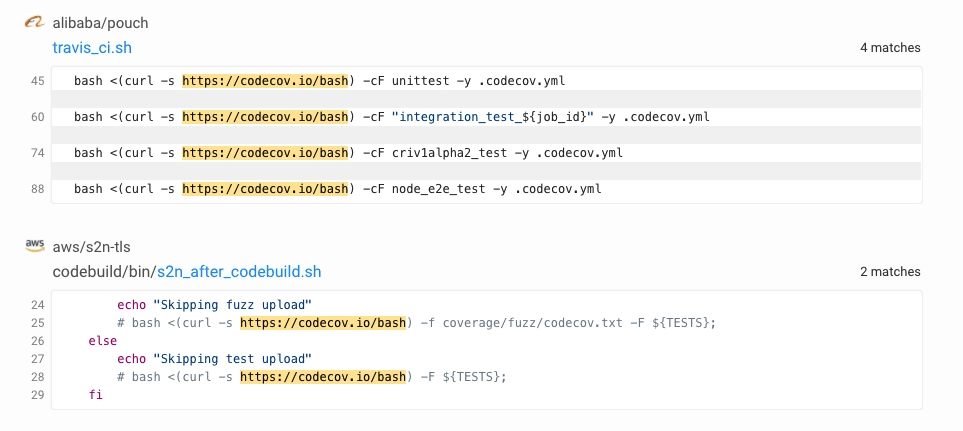
The Bash Uploader script is used by Codecov customers to send code reports to the server. It detects specific settings, collects reports, and uploads.
Hackers focused on this data in their attack campaign, effectively changing the address to where the data was sent – To a server outside Codecov. Due to the data collected by the hackers, Codecov announced that the threat actors could be in possession of any of the following:
- Any credentials, tokens, or keys that our customers were passing through their CI runner that would be accessible when the Bash Uploader script was executed
- Any services, datastores, and application code that could be accessed with these credentials, tokens, or keys
- The git remote information (URL of the origin repository) of repositories using the Bash Uploaders to upload coverage to Codecov in CI
Because of this potential risk, affected users are strongly recommended to re-roll all credentials, tokens, or keys present in the environment variables in the CI processes that relied on Bash Uploader.
Customers using a local version of the script should check if the hackers code added at line 525 exists. If the code below is present, they should replace bash files with Codecov’s latest version of the script.

Regarding the attack, Codev said, “Based upon the forensic investigation results to date, it appears that there was periodic, unauthorized access to a Google Cloud Storage (GCS) key beginning January 31, 2021, which allowed a malicious third-party to alter a version of our bash uploader script to potentially export information subject to continuous integration (CI) to a third-party server. Codecov secured and remediated the script April 1, 2021”
Immediately after learning of the compromise, the company took steps to mitigate the incident, which included the following:
- rotating all relevant internal credentials, including the key used to facilitate the modification of the Bash Uploader
- auditing where and how the key was accessible
- setting up monitoring and auditing tools to ensure that this kind of unintended change cannot occur to the Bash Uploader again
- working with the hosting provider of the third-party server to ensure the malicious webserver was properly decommissioned
Hackers Draw Attention of US Federal Investigators

By mid-April, the scale of the attack had grown so much that it had gotten the attention of US Federal Investigators, and comparisons were made to the SolarWinds breach last year. CodeCov have around 29,000 customers, making the attack potentially catastrophic.
According to federal investigators, Codecov hackers deployed automation to use the collected customer credentials to tap into hundreds of client networks, thereby expanding the scope of this system breach beyond just Codecov’s systems.
By abusing the customer credentials collected via the Bash Uploader script, hackers could potentially gain credentials for thousands of other restricted systems, according to the investigator.
Some Codecov customers such as IBM stated they have not been breached by the hackers, but have declined to comment further.
An Atlassion spokesperson said, “We are aware of the claims and we are investigating them. At this moment, we have not found any evidence that we have been impacted nor have identified signs of a compromise.”
Hewlett Packard Enterprise claimed their investigation was continuing, “HPE has a dedicated team of professionals investigating this matter, and customers should rest assured we will keep them informed of any impacts and necessary remedies as soon as we know more”
The Federal Bureau of Investigation and the U.S. Department of Homeland Security have not commented on the investigation at this time.
The Codecov is yet another supply-chain attack we’ve seen recently. In the last 12 months, these kinds of attacks have become increasingly common, allowing hackers to breach a multitude of enterprises through one weakest link.
Protection
With many supply-chain attacks occurring, it is important that businesses and families have the best possible tools to keep themselves protected. One of these tools is SaferNet.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.