Malware’s primary obstacle when it comes to mobile devices has always been the infection vector – The act of physically placing itself on a device. Hackers have come up with novel, clever, and complex ideas in the past. None of these have ever been as successful as using a Dropper. An attack using droppers can go unnoticed for quite some time, as was the case with Google as they removed 9 apps from the app store recently. Each app was a host for Malware, issued by a dropper dubbed Clast82.
Droppers are nothing new; they have been active on PCs for many years, though lately have made the mobile market their new home. A dropper will first appear as a normal app with everyday use. This could be a calculator app, a fitness tracker, a media player, or just about anything. The hacker will develop a completely legitimate app to build trust with the community and with Google Play.
Google Play has several strict policies to ensure that apps are legitimate, so building trust is critical for a dropper to succeed.
Once this trust is built, the dropper becomes active. A backdoor will open within the app and change the underlying code, turning it from a seemingly innocent utility to fully-fledged Malware. This bait-and-switch attack vector has sometimes been called a Quasi-Trojan; Like a trojan, it masks a more serious payload. Unlike a trojan, that payload is not present until the hacker decides to activate the backdoor.
The 9 apps removed from the Play Store had some devastating functionality when activated, capable of gaining intrusive access to the financial accounts of victims and full control of their devices.
Clast82 deployed AlienBot Banker and Rogue onto devices that held any of the apps. AlienBot Banker is malware that focuses on harvesting banking credentials from a mobile device. It does this by injecting malicious code into banking apps found on the device, allowing the hacker to take control.
Rogue is an MRAT (Mobile-Remote-Access-Trojan). Rogue generally allows the hacker to control all aspects of the phone and spy on users’ inputs.
The 9 apps that were removed are Cake VPN, Pacific VPN, eVPN, BeatPlayer, QR/Barcode Scanner MAX, Music Player, tooltipnatorlibrary, and QRecorder.
Methodology

Clast82 used two primary techniques to bypass Google Plays detection and to upload Malware to the users device.
Firstly, it used FireBase as a platform for Command-And-Control (C&C).
Secondly, it used GitHub as a 3rd party hosting platform to download the payload from.
During Google Plays evaluation period of the apps, the configuration from the Firebase C&C contains an ‘enable’ parameter. Based on the value of the parameter, the malware will decide to trigger malicious behavior or not. During the evaluation, the parameter will be false. Once the period has finished and Google publishes the app, the parameter will change to true.
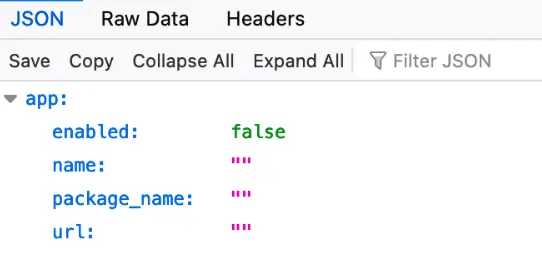
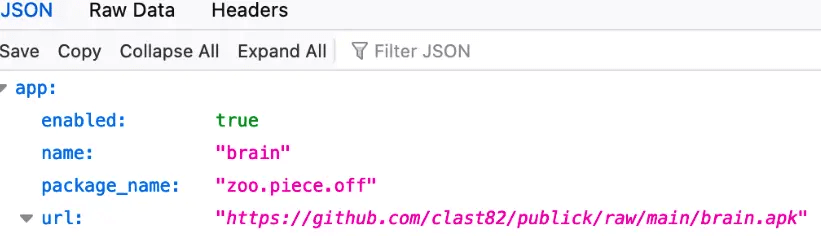
Cybersecurity researchers investigating the hackers github uncovered revealed they had created a new developer account for each app, along with different payloads of each of the 9 apps. This allowed them to deploy varied payloads as desired to each app.
With this system in place, an attack followed 5 steps:
- Hacker Uploads To Google Play.
- Googles’ evaluation is met with a False parameter at the Firebase C&C – No malware is present.
- Google approves the app.
- Victims install apps, which contacts the Firebase C&C. The parameter changes from False to True.
- The device contacts the hackers Github and begins downloading Malware, unbeknownst to the user.
It is believed that the legitimacy of the apps as they were approved stems from the hacker using open-source libraries to develop the apps, effectively doing custom paint jobs on publicly available app source codes.
The Play Store as the Primary Attack Vector For Malware

A study in 2019 shed light on hackers using the Play Store as an attack vector Malware. It was found that the Play Store was infact the largest carrier for Malware on Android systems, and found that 67% of malicious apps came from Google’s Play Store. This number debunks the theory that third-party app stores such as Aptoide and APKMirror were harbingers of malware apps – These stores accounted for just 10% of malicious payload deliveries.
The same study analyzed 34 Million app installations for 7.9 Million unique apps. It found that between 10% and 24% of the apps analyzed contained some form of unwanted Malware.
These attacks are making the headlines more frequently it seems.
In February 2020, Google removed 56 apps from the Play Store, which infected 1.7 Million devices with Malware. July 2020 saw the rise of the Joker Malware on the Play Store, a devastating phishing program. PhantomLance, a notorious mobile Spyware platform, successfully carried out a 5-year campaign on the Play Store, which was just discovered a few months ago.
What You Can do For Protection
Protection against Droppers like Clast82 can be tricky because in most cases the user is unwillingly inviting Malware onto their device. As is the case with most forms of cybersecurity defense, knowledge is your key weapon.
When downloading an app from the Play Store, don’t hit ‘Install’ without taking some precautionary steps:
- Research the developer. Do they seem legitimate?
- Read the reviews. Remember that sometimes hackers will leave fake reviews – Be aware of this, and use your intuition.
- Read the permissions before you download. If you feel uncomfortable giving an app as much access as it requests, don’t download!
Along with these steps, users should use the proper security tools to ensure their device is safe. One of these tools is SaferNet.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.