The Gafgyt botnet, known for attacks using IoT devices, has absorbed code from the Mirai botnet. The latter also focuses on using IoT devices in its arsenal and released its code publicly several years ago. Researchers have discovered updated variants of Gafgyt using several functions ripped straight from Mirai, allowing Gafgyt to compromise Huawei, Realtek, and Dasan GPON devices. The botnet was already known to target devices from ASUS and other large IoT manufacturers. It also often uses known vulnerabilities such as CVE-2017-17215 and CVE-2018-10561 to download next-stage payloads to infected devices.
The latest variants have now incorporated several Mirai-based modules, according to research from Uptycs released last Thursday, along with new exploits. Variants of Mirai, and indeed other botnets re-using Mirai modules have become more common since the developers released the code base in 2016.
The capabilities taken from Mirai including different methods to carry out DDOS attacks:
HTTP flooding is a kind of DDoS attack in which the attacker sends a large number of HTTP requests to the targeted server to overwhelm it. The creators of Gafgyt have re-used this code from the leaked Mirai source code.

UDP flooding is a type of DDoS attack in which an attacker sends several UDP packets to the victim server as a means of exhausting it. Gafgyt contained this same functionality of UDP flooding, copied from the leaked Mirai source code.

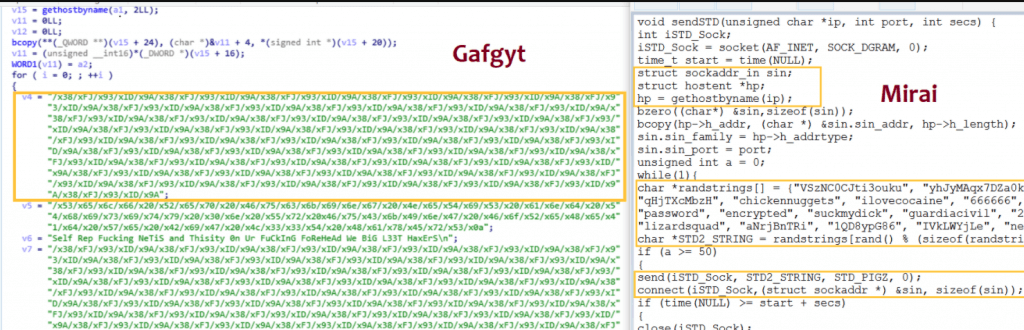
TCP flood module – Gafgyt performs all types of TCP flood attacks like SYN, PSH, FIN, etc. In this type of attack, the attacker exploits a normal three-way TCP handshake the victim server receives a heavy number of requests, resulting in the server becoming unresponsive. The below image shows the TCP flooder module of Gafgyt, which contained the similar code from Mirai

STD module – Gafgyt contains an STD module which sends a random string (from a hardcoded array of strings) to a particular IP address. This functionality has also been used by Mirai.
Brute force module – Not only are flooding modules are being used. Recent Gafgyt also contained other modules with little tweaks, like a telnet bruteforce scanner

Meanwhile, the latest versions of Gafgyt contain new approaches for achieving initial compromise of IoT devices, Uptycs found; this is the first step in turning infected devices into bots to later perform DDoS attacks on specifically targeted IP addresses. These include a Mirai-copied module for Telnet brute-forcing, and additional exploits for existing vulnerabilities in Huawei, Realtek and GPON devices.
Gafgyt botnet uses the Huawei exploit (CVE-2017-17215) and the Realtek (CVE-2014-8361) exploit for remote code execution (RCE), which is used to fetch the Gafgyt payload.
“The Gafgyt malware binary embeds RCE exploits for Huawei and Realtek routers, by which the malware binary, using ‘wget’ command, fetches the payload,” according to Uptycs. “[It] gives the execution permission to payload using ‘chmod’ command, [and] executes the payload.”
The GPON exploit (CVE-2018-10561) is used for authentication bypass in vulnerable Dasan GPON routers; here, the malware binary follows the same process, but can also remove the payload on command.
“The IP addresses used for fetching the payloads were generally the open directories where malicious payloads for different architectures were hosted by the attacker,” researchers added.
Before Gafgyt Botnet: The Storied History of Mirai
The Mirai Botnet has been around for several years. While other malware may go into periods of slow activity, Mirai has remained at the forefront of botnet headlines since its inception.
Perhaps Mirai’s most infamous attack came on October 12, 2016. On that date, a massive denial of service (DDoS) attack left much of the internet inaccessible on the U.S. east coast. The attack, which authorities initially feared was the work of a hostile nation-state, was in fact the work of the Mirai botnet.
This attack, which initially had much less grand ambitions grew more powerful than its creators ever dreamed possible. The origins of the botnet were speculated for some time, many believing it to be the work of high-profile cybercriminals. Instead, Mirai was created by a group of three friends who were using the botnet to run an extortion ring on Minecraft servers, a video game they played together.
It encapsulated some clever techniques, including the list of hardcoded passwords. But, in the words of an FBI agent who investigated the attacks, “These kids are super smart, but they didn’t do anything high level—they just had a good idea.”
Much more damaging than simply developing the botnet, the creators released the source code publicly in 2016. This has lead to a wild fire of Mira-related attacks, and researchers estimate there are more than 60 variations of the botnet currently.
Mirai has a few key characteristics seen across all variations of it:
- Mirai can launch both HTTP flood and network-level attacks
- There are certain IP address ranges that Mirai is hard-wired to avoid, including those owned by GE, Hewlett-Packard, and the U.S. Department of Defense
- Upon infecting a device, Mirai looks for other malware on that device and wipes it out, in order to claim the gadget as its own
- Mirai’s code contains a few Russian-language strings. This was intended to be a red-herring on its origin, but still remains in variations
Protection
With evolving botnet tools like Gafgyt posing new threats every day, its important you use the tools required to protect your devices. One of these tools is SaferNet.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.