Ransomware is a lucrative business. While once a type of malware targeted mostly consumers, in the last decade, Ransomware has turned its sights on the business, financial, and government sectors. Though ever-evolving to new stages of complexity, the idea behind it is fairly simple. A computer, or phone, gets infected with Ransomware, and all the files on the device are locked up in a special type of encryption. The user will see a message on the screen from the hacker, stating that their files have been locked and must pay a sum of money for everything to be unencrypted.
It is most common for just files to be encrypted, but other types of Ransomware have been known to lock down entire operating systems.
The Cuba Ransomware was first sighted in late 2019 after infecting a number of individual machines. These incidents were not widely reported on, as they seemed to be isolated. It’s now thought the individuals behind this, known as the Cuba Ransomware Gang or just ‘Cuba Gang,’ were practicing and dipping their feet in the world of cybercrime.
Throughout 2020, the Cuba Ransomware was reported on several systems, though none major. However, the volume of reports that appear prompted cybersecurity researchers to publish data on the attacks’ exact nature.
Cuba Gang were marked as potential major threat actor, and in Feburary 2021 they lived up to their reputation.
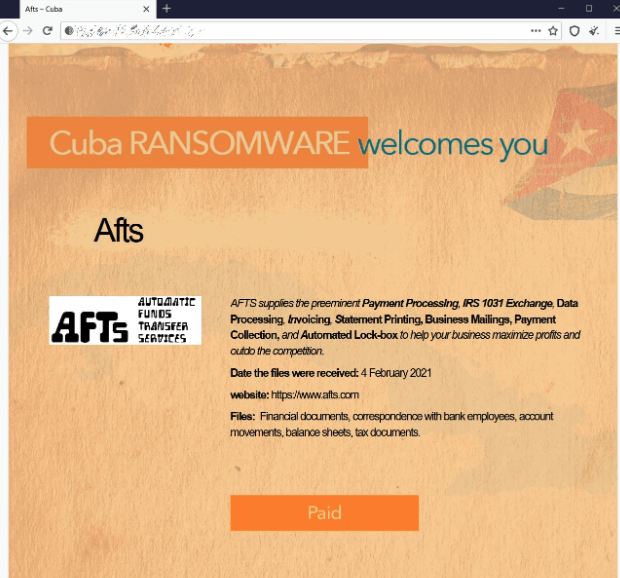
On the 4th, Cuba Gang attacked the Automatic Funds Transfer Services (AFTS). The AFTS are a billing and payment processing which operate out of Seattle. They operate with a number of local, municipal and state government entities in the state of Washington, but also across the United States.
Given the reach of the AFTS, it’s no surprise how many entities have been affected. The AFTS refused to pay the ransom on their data, and so Cuba Gang promptly transferred it back to their own servers to sell on the Dark Web.
For most cities using AFTS that were affected, the breach is not as destructive as it could have been. It is understood no Social Security Numbers were disclosed in the encrypted files; however, names, billing account numbers, addresses, and other categories of personal information have been. Within Washington, the following cities citizens are affected:
- Seattle
- Kirkland
- Monroe
- Lynnwood
- Lakewood
- Everett
The most notable victim in the attack is the California Department of Motor Vehicles, which used AFTS. It is believed the details of up to 38 Million citizens have been exposed, which are now being sold online for the purposes of identity theft.
The data exposed from the breach includes names, addresses, phone numbers, license plate numbers, VINs, credit card information, scanned paper checks, and billing details.
At the time of writing, the attack is still on-going, and more cities are finding themselves affected. The AFTS website is currently unavailable, and the authorities including the FBI are investigating the incident.
The Nature of Cuba Ransomware
Cuba targets only Windows devices, though it functions on all Windows OS versions from Windows XP to Windows 10, meaning it can penetrate legacy-server systems that many industrial institutes still use today to the most modern machines.
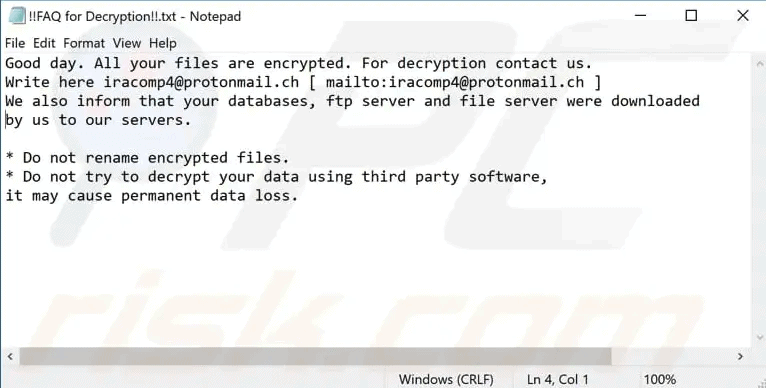
Once inside, the virus will encrypt all files with the .cuba extension, e.g., picture.jpg will become picture.jpg.cuba. These files will not be able to be opened by the victim while in this encrypted state.
The victim will be instructed via Notepad that if they want to decrypt their files, they will need to contact a protonmail based address to arrange the ransom – a money transfer to get the files back.
If the ransom is not paid, a backdoor within the virus activates. This backdoor funnels the encrypted files back to Cuba Gangs’ Command Center. Once decrypted on their side, the files are then sold on their website located on the Dark Web.
The full scale of this attack has not yet been revealed, what is clear though is that Cuba Gang have gone from small-time crooks to large-scale criminals. Given the success of their attack on AFTS, it is likely they will continue this campaign against US local governments for duration of 2021.
The Genesis of the Attack

No longer do hackers need to have extreme levels of technological literacy to start a campaign; instead, they can purchase or rent Malware on the dark web and begin in earnest.
Cybersecurity researchers have confirmed Cuba is the product of MaaS, being based on the Buran ransomware family.
Buran surfaced on a Russian dark web forum in early 2019, named for the Buran-class orbiters developed by the Soviet Space Program.
Buran is sophisticated ransomware known for its high speed and ability to easily bypass defenses and burrow into Windows system directories.
Before the advent of Buran, the MaaS space was dominated by big hitters such as REVil, GrandCrab, and Phobos. Some of these worked on a commission basis, their customers having to pay as much as 40% of their take back to the developers.
Buran started a price war in the scene, offering rates of 15-25% based on the volume of attacks.
Many ransomware clients have used the Buran core. It’s possible that if Cuba Gang continues their efforts throughout the year, they could be its most infamous user.
How You Can Stay Protected Against Ransomware

2021 has started on ominous footing for the cybersecurity world and arming yourself, or your business with the right defensive tools against threats like ransomware now is the secret to that preparation.
SaferNet was created as a way to defend against the threats of today and those of tomorrow.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.
Try SaferNet Now