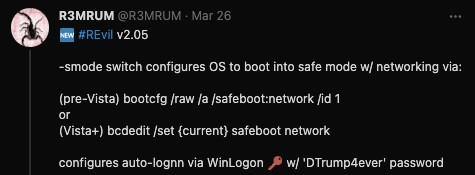
Evil Ransomware, already a major threat in the world of cybersecurity, has gotten a new update to give it extra fangs. In March, the Ransomware was developed further to give it the ability to encrypt in safe mode. This mode can be enabled using the -smode command-line argument, which would reboot the device into Safe Mode, where it would perform the encryption of files. However, the ransomware required someone to manually login to Windows Safe mode before the encryption would start, which could raise red flags. This week, another update came for REvil. This time, the ransomware was able to change the login credentials and cause an automatic re-log after restarting, fully automating the infection process.
It is believed that these features were added to REvil Ransomware in order to evade detection by the hosts cybersecurity software. Furthermore, it would shut down backup software, database servers, or mail servers to have greater success when encrypting files.
The updates were reported on and analysed by security researcher R3MRUM.
REvil, upon infection, will edit several settings within the Windows Registry. Specifically, it sets the auto-login to “1”, the default user name to the account name, and the password to “DTrump4ever”.
It is unknown if all samples of REvil Ransomware will use this password, however at least two uploaded to VirusTotal have it enabled.
REvil has been at the forefront of ransomware attacks for a long time, and this update will ensure it remains there. The gang grew more aggressive in recent attacks; when victims refused to pay, they called journalists to report the companies breach. There have also been several reports since the start of 2021 of the gang threatening victims with DDOS attacks if they don’t pay up.
REvil Ransomware: A Storied History

REvil is a Ransomware-as-a-Service (RaaS), meaning it can be sold on a subscription basis and is usable by just about anybody. In the last 12 months, it has extorted large amounts of money for corporations and individuals. According to researchers, it is the most widespread ransomware strain. Groups using have a knack for shaking down businesses that don’t meet their demands, often through threats or leaking dating.
REvil, also known as Sodinokibi, first appeared in April 2019 and rose to prominence after another RaaS gang called GandCrab shut down its service. In the early days of REvil, researchers and security firms identified it as a strain of GandCrab, or at least established multiple links between the two. An alleged member of the group, using the handle Unknown, confirmed in an interview that the ransomware was not a new creation and that it was built on top of an older codebase that the group acquired.
The group behind REvil Ransomware and other groups selling RaaS often do so on a commission basis. Usually, this means a cut of between 20% and 30% of the money earned through infecting victims with ransomware.
In 2020, the IBM Security X-Force Incident Response reported that 1 in 3 Ransomware infections were caused by REvil.
In February, the REvil ransomware operation posted a job notice where they were looking to recruit people to perform DDoS attacks and use VOIP calls to contact victims and their partners.
In March, a security researcher known as 3xp0rt discovered that REvil has announced that they were introducing new tactics that affiliates can use to exert even more pressure on victims.
These new tactics include a free service where the threat actors, or affiliated partners, will perform voice-scrambled VOIP calls to the media and victim’s business partners with information about the attack. The ransomware gang is likely assuming that warning businesses that their data may have been exposed in an attack on of their partners, will create further pressure for the victim to pay.
REvil is also providing a paid service that allows affiliates to perform Layer 3 and Layer 7 DDoS attacks against a company for maximum pressure. A Layer 3 attack is commonly used to take down the company’s Internet connection. In contrast, threat actors would use a Layer 7 attack to take down a publicly accessible application, such as a web server.
Protection
For threats like REvil, it is important to have a proactive approach, rather than reactive. Reactive cybersecurity is effectively useless against threats like this, when a device can be rebooted in safe mode immediately. It is critical that business leaders use proactive tools like SaferNet to ensure their businesses are protected.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.