Ransomware is a type of malware that encrypts a victims device entirely and then demands a monetary fee, or ransom, for the safe release of the data. During this time, the victim cannot access any of their files. Ransomware is a sophisticated type of virus, and will often laterally spread across a network, allowing it take down large scale organizations like hospitals in seconds. Though it only became more popular in the last decade, Ransomware has become the number one threat in the cybersecurity world. Ransomware operators can generate billions of dollars in a successful attack campaign.
Owing to its sophistication is the encryption Ransomware uses, namely asymmetric. This cryptography uses a key pair to encrypt and decrypt files, and are unique. The private key is used for decryption, and this is what is handed over if the ransom is paid. While in the majority of cases decryption has been impossible without the private key, there has been attacks tha savvy researchers were able to foil by reverse-engineering the ransomware strain and revealing the private key.
There are hundreds if not thousands of ransom variants. The most common attack vector is through phishing, but there a litany of other methods also.
Once files have been encrypted, the ransomware will leave a ransom note on the system, explaining the terms of the ransom to the victim. Usually they are given a short window to comply – 24 to 72 hours is most common.
If a data backup is not available, or the backup has been encrypted, the victim will need to pay to recover the attacks.
In the last decade, new technology has allowed ransomware to flourish. Malware kits are cheap to buy, and allow hackers to create strains instantly.
In fact, many ‘hackers’ behind Ransomware aren’t hackers at all. Ransomware is sold online (Known as Ransomware as a Service, or RaaS) for a cheap price, and a portion of the profits are given to the developer.
Cryptocurrency has long been the payment method for Ransomware, given it anonymous nature.
Ransomware has only gone from strength to strength, and given its ability to generate cash for its operators, it’s unlikely to go anywhere soon. It has been used in corporate attacks, attacks on the home, and very often in cyber warfare between nations. Today, we’ll look at some of the biggest Ransomware attacks that occured over the summer of 2022.
The History of Ransomware

Despite its surge in popularity in recent years, the genesis of Ransomware occured quite a long time ago. In the 1980s, one of the first ransomware strains appeared, dubbed the AIDS trojan. It was issued via floppy disk, and victims would ned to send nearly 200 dollars to a P.O. box in Pana to restore access to their network. It was a fairly simple virus, using symmetric cryptography, but those simple beginnings wouldn’t take long to evolve.
Ransomware chugged a long for a few years, but the big issue was payments. In the 90’s and 2000s, payments were possible online but were in no way anonymous. This changed with the advent of cryptocurrency, Bitcoin specifically. This gave criminals the ability to demand ransoms anonymously. Cryptocurrency was the catalyst for ransomware to take the dominant spot amongst its malware peers.
The firstly truly sophisticated ransomware strain in this era was CryptoLocker, in 2013. Not only did it use cryptocurrency for payment, it came with a new type of encryption – 2048 RSA key pairs. The Ransomware also connected to a command-and-control center. Decryption of infected machines was available for $300.
Eventually, CryptoLocker was shut down by the FBI within 7 months of its inception. Despite this, it left a huge inprint in the hacker community.
Within months, CryptoLocker clones appeared all over the web. Older hacking gangs shifted focus – Instead of peddling adware or fake antivirus, everyone in the scene was now in the Ransomware game. The Dark Web marketplace exploded with illicit goods gotten from ransomware attacks.
Ransomware attacks began more percise. Instead of tossing a net out, savvy malware developers focused in on large companies and organizations. This lead to the big payouts – Ransom amounts in the millions.
And since then, Ransomware has continued on this path. It only gets more sophisiticated, and the ransoms only get bigger.
Italian Energy Provider Taken Out

Italy’s national energy service, the GSE, was recently hit by the Blackcat/ALPHV ransomware gang. GSE is publicly owned, and supplies renewable energy across the country. A spokesperson for the company stated that its websites and systems were taken offline in an attempt to halt the spread of the ransomware across the network. These systems were offline for over a week.
Italian authorities are still investigating the issue, and researchers are still trying to determine what data was compromised.
Before GSE disclosed details of the attack, BlackCat added a new entry to its leak site, which was claimed to be over 700GB of files from the energy company – A sizeable amount of data.
According to the hackers, they stole confidential data, including contracts, reports, project information, accounting documents, and other internal documentation.
The GSE attack comes not long after a similar attack on another Italian energy company with over 31,000 employees. This attack had less severe effects on the company.
BlackCat are no strangers to ransomware attacks on energy companies. Earlier in the year, they attacked Creos Luxembourg S.A., a central european pipeline company. Around this time they also hit German petrol company Oiltanking.
BlackCat launched in Novemeber last year. Most believe it to be a rebranding of the Darkside gang.
Darkside was taken offline last year after the Colonial Pipeline attack, which drew the spotlight from the FBI.
Darkside/Blackcat are considered one the best and most lethal ransomware gangs operating in the world currently. Hitting energy companies across Europe, especially when the Union is in an energy-crisis, shows that its operators will stop at nothing to get a sizeable ransom.
BlackCat also began deploying extortion tactics lately, and launched a searchable database with all its victims for information-buyers.
In April, the FBI warned that BlackCat has “extensive networks and experience with ransomware operations” as they had breached more than 60 entities worldwide between November 2021 and March 2022.
Clothing Giant Damart Face Hive Ransomware Gang
The French clothing company, Damart, has been hit in a ransomware attack by the Hive ransomware gang, who demanded $2 million. The company has nearly 150 outlets around the globe.
Many of Damarts systems have been encrypted since mid-August, and operations have largely been disrupted.
The ransom note was leaked and made it into the hands of reporters at LeMagIT. The note states that negotiation is off the table, and payment should be made in full.
Damart has not attempted to contact the hackers yet, but the police are aware of the incident. This makes it unlikely that the payment will be made.
The initial infection appeared on August 15th, when Damart disclosed that they needed to perform an unscheduled maintenance of its homepage.
Reporters at BleepingComputer reached out to Damart, who responded with the follow:
“Damart, the mail order clothing brand, based in Bingley, West Yorkshire, has confirmed that there was an attempt to intrude into their IT systems, which they were rapidly able to intercept with strong security protocols.
“As a precaution, they have temporarily restricted some services available to customers, which is why the website is currently offline. Data and system security is a top priority for the business and reassuringly there is no evidence to-date that any customer data has been impacted in any way.”
By August 24th, almost 100 of its stores were impact by the attack. Customer support was unavailable, and online orders had decreased dramatically.
The company claim the systems are performing slowly due to proactive measures taken to halt the spread of infection.
It is unknown if Hive stole data during the attack – At present, there is nothing relating to Damart on their leak website.
Chilean Government Struggle Against Infection

CSIRT, the computer security government entity for Chile, has disclosed that a ransomware attack severely disrupted the online services of a government agency within the country. The attack began on August 25th, and lashed out at Microsoft and VMware ESXi servers.
The hackers halted all running virtual machines, and encrypted every file on the machines.
“The ransomware would use the NTRUEncrypt public key encryption algorithm, targeting log files (.log), executable files (.exe), dynamic library files (.dll), swap files (.vswp), virtual disks (. vmdk), snapshot (.vmsn) files, and virtual machine memory (.vmem) files, among others,” the agency stated.
The ransomware used in the attack is sophisticated and multi-faceted, also showing capabilities of credential harvest from browsers, and antivirus evasion using execution timeouts.
The hackers employed double-extortion, and established a comms channel with CSIRT. The promise was that payment would prevent the leaking of files and the trade of a decryptor.
The attackers gave CSIRT a 3 day deadline to payout.
CSIRT have yet to identify the group responsible.
The extension used to encrypt the files (.crypt) doesn’t supply any clues either, as it is a common extension in the ransomware scene.
However, some researchers believe that the attack was caused by the RedAlert ransomware, which appeared in July 2022. The attack has many of their recent hallmarks.
Still, not everybody agrees. Chilean analyst Germán Fernández told researchers at BleepingComputer the strain is entirely new.
“One particular thing about the attack, is that the threat actors distributed the ransom note at a previous stage to the deployment of the ransomware as the final payload, possibly for evasion issues or to avoid having their contact details leaked when sharing the final sample.” Fernández said.
Airline Face Ragnar Locker
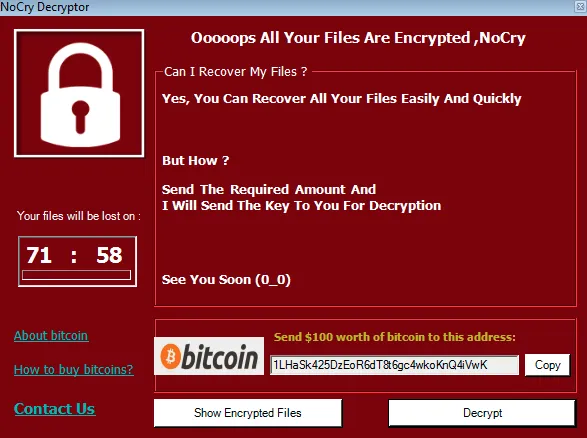
TAP Air Portugal, the countries largest airline, was recently hit by the Ragnar Locker ransomware. The company stated that the attack was blocked, and added that it had no evidence that the hackers gained access to customer information.
“TAP was the target of a cyber-attack, now blocked. Operational integrity is guaranteed,” the airline operator revealed in a statement on Friday via its official Twitter account.
“No facts have been found that allow us to conclude that there has been improper access to customer data. The website and app still have some instability.”
Despite this, the airline took its website and app offline due to the cyberattack, likely as preventative measure. To keep airport queues moving, TAP allowed passengers to book flights, manage books, and download boarding passes without logging into the app.
Despite TAPs statement that no customer data had been leaked, the Ragnar Locker Ransomware gang have posted a new entry concerning TAP on their leak site.
The gang claim to have hundreds of gigabytes from the attacks, and threaten to provide evidence to disprove TAP.
“Several days ago Tap Air Portugal made a press-release where they claimed with confidence that they successfully repelled the cyber attack and no data was compromised (but we do have some reasons to believe that hundreds of Gigabytes might be compromised),” the gang says.
The gang also shared a screenshot of some of the information stolen.
Ragnar Locker ransomware is no stranger in Portugal, where it previously struck energy giant EDP, with a $10 million ransom.
TAP have yet to comment further.
Healthcare As A Prime Ransomware Target
The Center Hospitalier Sud Francilien (CHSF), a large Parisian hospital, was hit by a large scale ransomware attack in recent weeks, which caused outages to the point that the staff had to postpone surgeries and refer patients to other hospitals.
CHSF has one thousand beds, and serves an area of 600,000 individuals, making it one of the cities busiest hospitals.
“This attack on the computer network makes the hospital’s business software, the storage systems (in particular medical imaging), and the information system relating to patient admissions inaccessible for the time being,” explains CHSF’s announcement.
The administration did not provide further updates, and the outage is still causing issues for the hosptial.
Currently, patients will be evaluated by CHSF doctors, and if they require treatment, they will be transferred to another medical center.
According to reporters at Le Monde, the ransom amount stands at $10,000,000.
“An investigation for intrusion into the computer system and for attempted extortion in an organized gang has been opened to the cybercrime section of the Paris prosecutor’s office,” a police source told Le Monde, also specifying that “the investigations were entrusted to the gendarmes of the Center fight against digital crime”.
French researcher Valéry Riess-Marchive believes the strain to be LockBit 3.0. He belives Ragnar Locker Ransomware is unlikely due to a different target group, whereas LockBit 3.0 has a broader targeting scope.
If it is LockBit 3.0, the attack violate the RaaS program rules, which disallows attacks on healthcare providers.
RansomEXX Hits Canada
The RansomEXX ransomware gang has claimed responsibilty for a devestating attack which occured on August 8th. The attack was aimed at Bombardier Recreational Products (BRP), a manufacturuer of Ski-Doo snowmobiles, Sea-Doo jet skis, ATVs, motorcycles, watercrafts, and Rotax engines. The BRP stated all their operations were to temporarily cease due to the attack.
As well as customer orders, production was also stopped.
The Canadian company employs over 20,000 people, and has an annual income of nearly $6 billion. The company is active in over 120 countries.
BRP also stated that even a minimal disruption would be extremely costly.
By August 15, manufacturing sites in North America and Europe were operational, with additional sites to follow.
BRP disclosed information which stated that the attack was a result of a supply chain strike.
“The Company confirms that the malware infiltration came through a third-party service provider. BRP believes that the impact of the cyberattack was limited to its internal systems,” the company states.
“At this time, while the investigation is still ongoing, it has not revealed any evidence that its clients’ personal information would have been affected by the attack”
BRP has said that they will notify individuals and corporations directly if the data breach uncovers more information.
The gang listed BRPs data on their leak site, which was almost 30GB big.
The information contained non-disclosure agreements, passports and IDs, material supply agreements, contract renewals, and more. This kind of data is some of the worst that can be leaked. The level exposure here is damaging for BRP. Stock of the company fell almost 7% since the attack.
“BRP confirms that it has already contacted the very few employees who may have been impacted by the incident. The appropriate resources have been made available to them, including credit monitoring services”
“Based on the current status of its investigation, BRP also believes that the compromised information relating to certain of its suppliers is limited in quantity and sensitivity, and is in the process of contacting them,” the company added.
Risk Mitigation For Ransomware
Becoming infected with Ransomware is likely the worst thing that can happen to your device. The steps to avoid Ransomware largely rest in preventative steps taken beforehand.
Backing up data is always a sound idea. Incase of an attack, a user, business, or organization can quickly restore their system. It is important that these backups are kept off local machines, as they are likely to get infected themselves.
Education and safe surfing are also key to protection. Be aware of phishing lures and malicious websites. These are the initial steps of infection in many cases, especially with regards to spear phishing against businesses.
Keep applications and Operating Systems up to date; this protects against zero-day vulnerabilities which can lead on to Ransomware infections.
Last, but certainly not least, use a cybersecurity solution, like SaferNet. SaferNet has been engineered to defend against many attack vectors used by Ransomware operators, including phishing attempts, malicious websites, and drive by downloads.
When it comes to Ransomware, you can’t afford not to be vigilant.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.