The Flubot banking trojan is actively attacking countries in Northern Europe, spreading via Android phones that are sending millions of malicious text messages. The attacks are mostly occurring in Finland.
Last week, the National Cyber Security Centre (NCSC-FI) at the Finnish Transport and Communications Agency disclosed a “severe” alert about rising Flubot malware infections.
Once Flubot is deployed on a phone, it goes about gaining permissions, stealing banking information and credentials, lifting passwords stored on the device and extracting away various pieces of personal information. It also self-replicates by sending out additional text messages from the infected host. Just like the regular flu, flubot uses a similar logic to become “viral”
“An Android malware called Flubot is being spread by SMS. According to our current estimate, tens of thousands of messages have been sent to people in Finland during one day. We expect the amount to increase in the coming days and weeks,” said Aino-Maria Väyrynen, information security adviser at the NCSC-FI, in the alert.
As Väyrynen predicted, the campaign did grow in numbers. An article published by Bloomberg on Tuesday quoted Väyrynen as saying the daily messages were now in the millions.
The country’s biggest telecom companies told the news outlet that they’ve intercepted hundreds of thousands of messages. Teemu Makela, CISO at Elisa Oyj, called the attack “extremely exceptional and very worrying.”
The NCSC-FI’s advisory said that the malware is targeting “everyone using an Android device and a mobile subscription,” while iPhones and other devices “are directed to other fraudulent material on the website.”
The malicious texts tell targets they’ve received a voicemail or a message from their mobile operator, however the containing link is malicious.
The link won’t install flubot right away – instead, targets are prompted to grant voicemail permissions, which is actually a front for malware installation. Once installed, Flubot goes about its business.
There are telltale red flags: The messages “are often written without Scandinavian letters (å, ä and ö) and may contain the characters +, /, &, % and @ in random and illogical places in the text,” the advisory explained.
Finnish authorities shared examples of the messages, as well as the malware’s installation request, both of which are shown below.
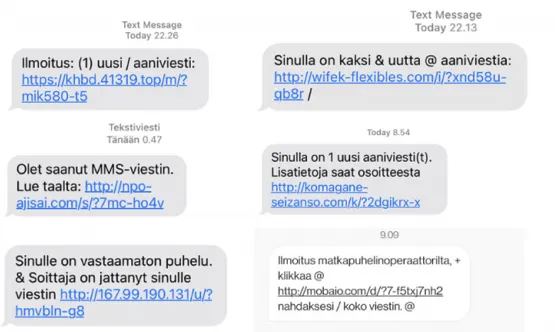
This is the second campaign in which Flubot recorded heavy infections across Finland. It first appeared in June 2021, and persisted into August. The ploy of the earlier campaign involved trying to trick the user into clicking a link concerning a missed package delivery.
That time, thanks to cooperation between the authorities and telecoms, the NCSC-FI said that the country managed to eliminate Flubot “almost completely.”
Atti Turnun, frad manager with Telia, spoke to Bloomberg and stated that this time the infection is far worse. The new wave shows that the Flubot operators have mutated their malware to hook its tentacles into victims regardless of the control measures put in place to eradicate the summer Flubot campaign, the security center said.
Hank Schless, senior manager of security solutions at Lookout, spoke to reporters with Threatpost and said that Finland’s plight is an example of “the problems that the malware-as-a-service (MaaS) market creates for consumers and enterprises alike.”
This market has made malware and phishing kits “incredibly accessible for even the least skilled threat actors,” he said. “Usually, for a very small price, someone can go online and find one of these kits fully built and ready to be used. Once they acquire the kit, all the attacker needs to do is host it on a web domain then build a delivery mechanism. Most frequently, this mechanism is some form of message targeting mobile users because of the number of ways you can deliver a message to these devices via SMS, email, social media platforms, third party messaging apps, gaming and even dating apps.”
The only difference between Finland’s earlier Flubot campaign and this one are the different social-engineering hooks, he noted – a sign of how “socially engineered phishing attacks can continue to be effective over time.”
Phishing has become “the most concerning issue for every enterprise,” Schless observed. “Threat actors not only use it to steal login credentials, but deliver malware to devices and infrastructure as well. Lookout data shows that threat actors heavily target users through mobile channels such as SMS, social media platforms, third party messaging apps, gaming and even dating apps.”
“Once the attacker has those compromised credentials, they’re free to log in to any corporate app and move laterally through the infrastructure,” Schless continued. “This could lead to them exfiltrating or encrypting data for an eventual ransomware attack.”
Schless concluded by stating that intelligence was “king” when it came to protecting against any attacks, but especially ones like Flubot.
“Solutions backed by datasets with enough threat telemetry are the only way to detect and protect against these attacks before they can even reach the end user,” he said. “Since these campaigns typically run for a short amount of time, traditional security solutions will be too slow on the uptake. Pushing automated coverage against attacks like this as the malicious page when it’s being built, is the only way to mitigate the gap in protection.”
NCSC-FI offered some solutions on what to do in the case of a flubot infection on your device. The chief most solution is to perform a factory reset.
However, in the case that Flubot banking trojan has deeply infected a users device and attacked banking apps, the NCSC-FI said the following:
- If you used a banking application or handled credit card information on the infected device, contact your bank.
- Report any financial losses to the police.
- Reset your passwords on any services you have used with the device. The malware may have stolen your password if you have logged in after you installed the malware.
- Contact your operator, because your subscription may have been used to send text messages subject to a charge. The currently active malware for Android devices spread by sending text messages from infected devices.
Protection Against Flubot
There are several tools internet users should use to increase their online protection. One of these tools is SaferNet.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.