Ransomware has proved to be one of the key malware threats for 2021, only three months into the year. Veterans to the scene like Ryuk still propagate massively, while novices like 2019’s Cuba are making headlines. Among the well-known faces in the world of ransomware is a newcomer – Babuk. Babuk was discovered in January of this year and has hit five major industries – Transportation, Healthcare, Plastics, Electronics, and the Agricultural sector.
Of the attacks it has carried out, just one target has paid the ransom, $85,000. The target in question was Serco.
For those who have not paid, the data is already for sale on the Dark Web.
Babuk uses several attack vectors seen in other Ransomware. Primarily, it utilizes Spear Phishing. The organization behind Babuk gets the emails of managers and executives of a company and starts emailing them, pretending to be a supplier, distributor, or another trusted party. The emails will contain an attachment. Within the attachment will be a popular trojan loader; In two cases, Emotet and Trickbot were reported. Once the attachment is opened, and the trojan is executed, Babuk will deploy on the target machine.
Babuk has also penetrated systems by using exploits. There are fewer people more up-to-date on security news than hackers, who are routinely looking for news on exploits on servers and databases, particularly those relating to Windows systems. Exploits like these mean there’s no requirement to ‘hack’ into the system as such, but rather to walk through a door that’s been left open. One report of a Babuk infection has traced back to an exploit within Remote Desktop access.
Lastly, Babuk has found entry methods via credential purchases on the Dark Web. Corporate accounts, information, and email addresses are all for sale on the Dark Web. Researchers at McAfee claim that several breaches by Babuk have been a result of using stolen credentials like these.
Unsophisticated Ransomware

Despite the damage Babuk is causing, researchers at McAfee have noted that the ransomware is fairly unsophisticated compared to more complex malware like Ryuk.
Babuk uses a ChaCha8 stream cipher for encryption and Elliptic-curve Diffie-Hellman for key generation. This makes recovery of the files without paying the ransom difficult for certain, but this encryption level is fairly standard.
Though seemingly independent, Babuk does share some core functionality seen in other Ransomware-as-a-Service (RaaS) products. Research points to the likelihood that the gang behind Babuk bought RaaS and have since reverse-engineered it and began to make it their own.
Babuk also contains a number of noticeable bugs, as well as lacking the obfuscation required for large-scale Ransomware campaigns. The researchers have stated the group behind the attacks has, “limited ransomware coding experience.”
Finally, Babuk contains no local-language checks. Often, Ransomware will check the language of the device before deploying. As a general rule of thumb, it will not deploy if the devices’ language is Russian or other Eastern European languages.
Recruitment in the RaaS World
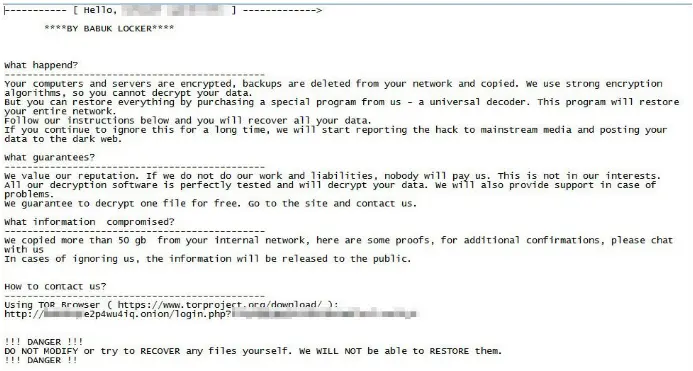
Ransom Letter Left by Babuk
As mentioned, the Babuk group seem to be reverse engineering RaaS in order to make it their own.
Attempts at this so far have certainly led to monetary gain, but as the researchers pointed out, the Ransomware itself is not very complex.
The group is seemingly aware of their limitations and has begun recruitment drives on the Dark Web.
Specifically, the Baruk group have begun hiring individuals skilled in ‘winPEAS, Bloodhound, SharpHound, CobaltStrike, and Metasploit’. This list of tools points to them hiring penetration testers, who will likely be tasked with enhancing Baruks’ capabilities to breach a system.
Due to this, McAfee has noted cybersecurity administrators should be on the lookout for suspicious behavior in non-malicious tools, such as PowerShell.
Protection Against Ransomware
As the criminals are gearing up in their recruitment, SMBs and individuals should be gearing up their arsenal of tools to protect against Ransomware like Babuk.
One of these tools is SaferNet.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.