The BazarLoader Malware is engaging in a campaign that targets users of work collaboration tools Slack and Basecamp. The attack utilizes email messages with links to malware payloads. Slack is a popular tool used for communication amongst teams, particularly those who work remotely. Basecamp focuses on project management but also allows for team communication. Similar to Slack, Basecamp is popular amongst remote workers. Both tools are used even in office environments.
We have reported at length on BazarLoader at SaferNet, most recently last week, when the malware was being distributed as a part of the BazarCall campaign. This campaign took a novel route by using call centers for social engineering.
The purpose of BazarLoader Malware is effectively to act as a Malware Loader. BazarLoader tends to distribute TrickBot, IcedID, Gozi IFSB, and other malware. Notably, it has also been distributing the notorious Ryuk Ransomware. These infections are hazardous as they provide remote access to compromised corporate networks where the threat actors spread laterally through the network to steal data or deploy ransomware.
“With a focus on targets in large enterprises, BazarLoader could potentially be used to mount a subsequent ransomware attack,” according to an advisory from Sophos, issued on Thursday.
According to researchers at Sophos, in the first campaign spotted, adversaries are targeting employees of large organizations with emails that purport to offer important information related to contracts, customer service, invoices or payroll.
“One spam sample even attempted to disguise itself as a notification that the employee had been laid off from their job,” according to Sophos.
The links in the malicious emails are hosted on Slack or Basecamp. This means that if the target uses either service, the link could appear legitimate. Given how popular these platforms and remote working have grown, this is likely.
“The attackers prominently displayed the URL pointing to one of these well-known legitimate websites in the body of the document, lending it a veneer of credibility,” researchers said. “The URL might then be further obfuscated through the use of a URL shortening service, to make it less obvious the link points to a file with an .EXE extension.”
If the victim clicks on the link, the BazarLoader malware downloads on the machine and is installed. These executable files, when run, inject a DLL payload into a legitimate process, such as the Windows command shell, cmd[.][exe].
“The malware, only running in memory, cannot be detected by an endpoint protection tool’s scans of the filesystem, as it never gets written to the filesystem,” explained researchers. “The files themselves don’t even use a legitimate .DLL file suffix because Windows doesn’t seem to care that they have one; The OS runs the files regardless.”
It is believed that BazarLoader is connected to Trickbot, in that the creators of each are possibly one and the same. TrickBot is another first-stage loader malware often used in ransomware campaigns.
Sophos looked into the connection and found that the two malwares use some of the same infrastructure for command and control.
“From what we could tell, the [BazarLoader] malware binaries running in the lab network bear no resemblance to TrickBot,” according to the posting. “But they did communicate with an IP address that has been used in common, historically, by both malware families. Of course, a lot of people have studied this connection in the past.”
In any event, BazarLoader appears to be in an early stage of development and isn’t as sophisticated as more mature families like TrickBot, researchers added.
For instance, “while early versions of the malware were not obfuscated, more recent samples appear to encrypt the strings that might reveal the malware’s intended use,” they said.
BazarLoader Malware Analysis

BazarLoader has been analysed in depth by cybersecurity researchers at AT&T Cybersecurity department.
The BazarLoader authors have produced an advanced module, with a significant amount of obfuscation. The BazarLoader uses multiple routines to hide API calls and embedded strings, which are then decrypted and resolved at runtime.
Once executed, the loader will allocate memory to store and decrypt its shellcode, which will be allocated to a NUMA node for faster execution. After allocation and decryption, the next instructions will jump to the shellcode that will be executed on the heap.
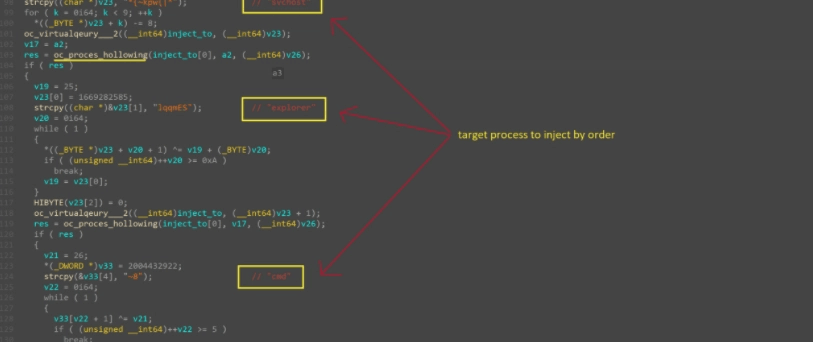
Next, the malware will try to communicate with .bazar domain C2 servers. Once the C2 has been established, the loader will try to inject its payload into a system process using the process hollowing technique (T1093), which will create a suspended thread, unmap the destination image from memory, allocate new memory in the target process, copy the shellcode into the target process, set the thread context, and resume the process.
The loader will first attempt to inject into an “svchost” process, and if injection fails, it will try to inject into the “explorer[.][exe]” process, and if injection fails again as a last-ditch effort the loader will attempt to inject into the “cmd[.][exe]” process. For persistence the loader will create a registry key under “HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit”.
The malware uses the Windows API “VirtualAllocExNuma” function to allocate memory for its shellcode to be executed. The “VirtualAllocExNuma” function is used to allocate memory on a NUMA node, which allows for faster execution. The implementation can be seen In Figure 1 below. It is interesting to note that the “VirtualAllocExNuma” function is not commonly used in process injection.

The BazarLoader authors have created dozens of decryption routines, and with almost each string including APIs, DLLs, and C2s there is a once per use unique decryption routine. The loader uses the same decryption technique described above to resolve the API calls it uses during execution.
For injection, the malware resolves APIs from the ntdll.dll after it loads from disk and checks that there are no inline hooks within its function, that could be created for example by AV software that tracks those API calls.
The load order of APIs called in the injection procedure is:
- CreateProcessA (CREATE_SUSPENDED | CREATE_NEW_CONSOLE)
- NtGetContextThread
- NtReadVirtualMemory
- NtUnmapViewOfSection
- VirtualAllocExA
- NtWriteVirtualMemory
- NtSetContextThread
- NtResumeThread
The obfuscated C2 servers are decrypted in the function shown below:

Protection
Education is also the key to defense against attacks like these. Outwitting social engineering attempts is the only guaranteed way not to fall victim to campaigns like BazarLoader. For times when a dupe may be unclear, it’s important to have the tools necessary to back you up. One of these tools is SaferNet.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.